The need to detect and mitigate denial-of-service attacks is nothing new to network and security administrators. DoS attacks on enterprise networks have been occurring for years.
A distributed denial-of-service (DDoS) attack overwhelms its target with a flood of traffic from malware-infected devices. It maxes out the capacity of the target host and blocks normal traffic to the host with a denial-of-service type of error. The direct cost of a DDoS attack in lost revenue or business opportunities can be staggering. And if the attack is a smokescreen for a data breach, businesses can lose much more.
Administrators need rapid detection and alarming when attacks are occurring. But they may also need to escalate to get the right people involved.
Good news! We’re going to set Plixer Scrutinizer up to share the offender list.
Our Scrutinizer analytics platform includes a suite of behavioral algorithms that can provide real-time DDoS detection of these types of events. We also provide a means to send email, syslog, or SNMP traps as part of a DDoS alarm notification profile. This detection and notification process has worked well for our customers over the years. But many customers that I’ve talked with lately are looking to not only detect these types of events as they are happening, but take direct action to mitigate these events.
The notification profile includes an option to call a script. In this blog, I will share a script that can be added to a notification profile. It will pick up the EventID of a DDoS or DRDoS alarm, then pull the violators (source IPs) for that DDoS or DRDoS alert, and write them to a file or pass them in a syslog message.
Setting this up will be a 3-part process
To start, here is the download link for the files.
Part 1: Copy files and set up parameters
- Unzip the DDoS-Notify-scripts.zip file to extract the getTheIPs.sh and DDOS-GetTheSources.py files
- Copy/upload both getTheIPs.sh and DDOS-GetTheSources.py files to the /home/plixer/scrutinizer/files/customScripts directory
- Change owner of both files to ‘plixer’ (chown plixer:plixer filename)
- Give Execute permissions to both files (chmod 755 filename)
- From the /home/plixer/scrutinizer/files directory, create a folder/directory to hold the source output files
- Create directory (mkdir ddos-src-lists)
- Change owner (chown plixer:plixer ddos-src-lists)
- Give Write permissions (chmod 777 ddos-src-list)
- Edit the following variables in the DDOS-GetTheSources.py file to match your environment
- Change the “ppass” variable to be the “plixer” user password
- Change the “slogserver” variable to = the IP address of the syslog server
- Set the “yeslog” variable for syslogs yes = (1) or no = (0)
Part 2: Move to the Plixer Scrutinizer web interface to create and configure a notification profile
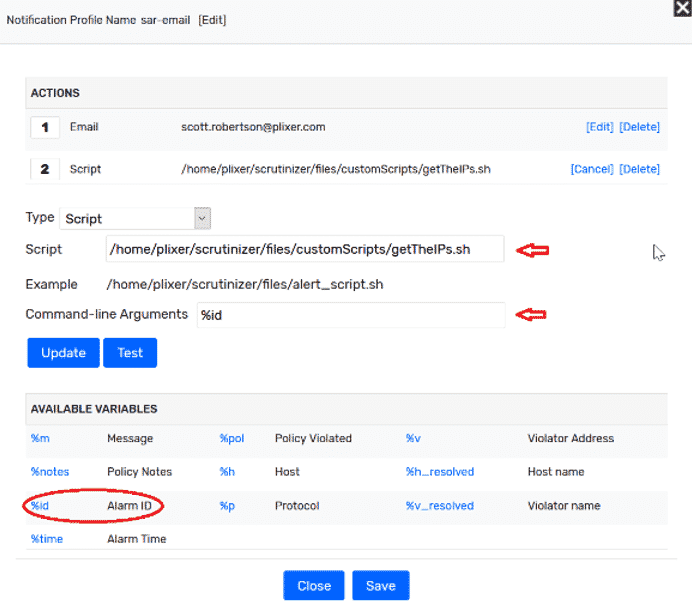
- In the webUI, go to the Admin tab > Definitions > Notification Profiles
- Click on Add button to add a new profile
- From the pop-up modal, name your new profile. Select the type of notification you want. (I send an email and call this script.)
- If email: simply select “email” from the Type pull-down list, and add the recipient email address, then hit Add. The policy is automatically saved.
- Now, select “script” from the Type pull-down list.
- Enter the path name to the script (/home/plixer/scrutinizer/files/customScripts/getTheISs.sh )
- In the command line box, enter – %id (alarmID)
- Hit Add
- Save and close
Part 3: Next we need to add our notification profile to the DDoS and DRDoS alarm policies
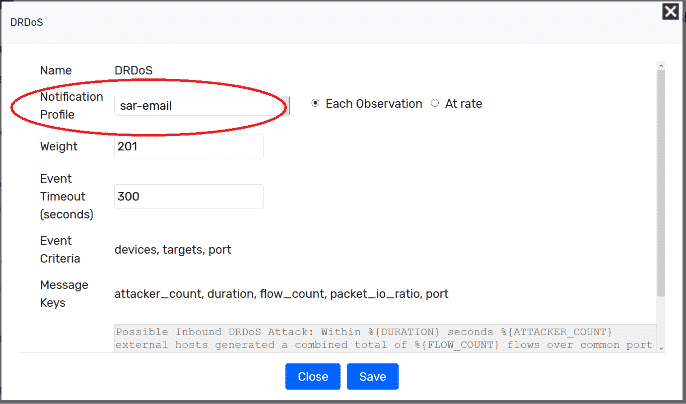
- Go to Admin > Definitions > Alarm Policies
- Select DDoS or DRDoS from the policy list
- Change the notification box so it reflects your notification profile and set to each violation
- Save
When the alarm triggers, you will receive an email with a subject and a message like:
Subject: Policy Violation:DRDoS
Message: AlarmID = 901843, –Violators = , — Possible Inbound DRDoS Attack: Within 60 seconds 8 external hosts generated a combined total of 1964 flows over common port 53 with a ratio of 128 inbound packets per outbound packet.
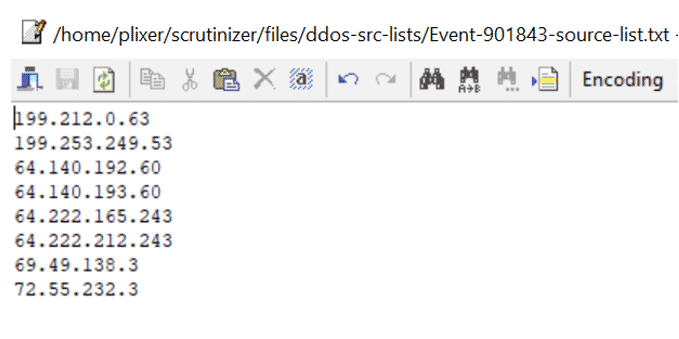
You will see output file(s) in the /home/plixer/scrutinizer/files/ddos-src-lists directory whose content will be the offending source IP address seen in the attack.
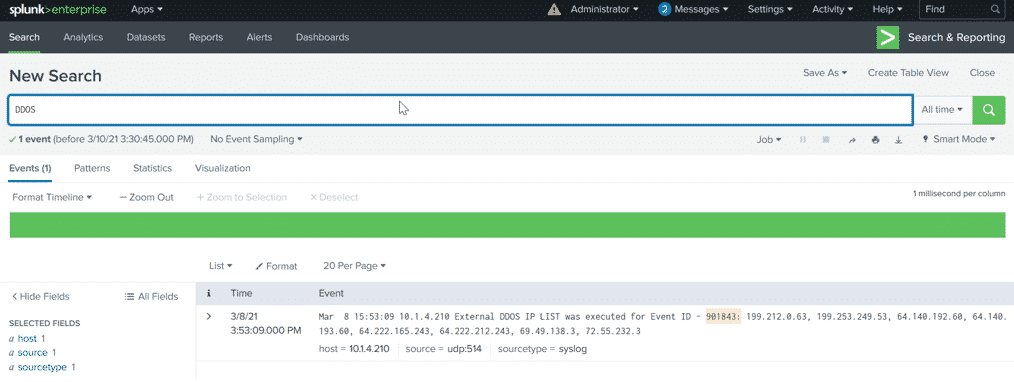
If you use the syslog option, you will see log entries that reference the EventID and the source list.
Do you need better traffic insight or an automated means to begin a mitigation process when denial of service type of attacks occurs? Reach out to us if you want to learn more or need help with setting this configuration up.
