Any security analyst will tell you that the most challenging part of the job is knowing what to respond to. There is no shortage of alarms or oddities that spark action in a security operations center. Being able to confidently prioritize your efforts is key to keeping your business safe from cyber threats.
MITRE ATT&CK® is a widely recognized and respected framework that helps security teams prioritize and understand the severity and progression of security incidents. It is essential for organizations to implement the ATT&CK® framework to manage and respond to security incidents effectively. The framework provides a comprehensive methodology for identifying, analyzing, and responding to incidents across an IT enterprise. Let’s discuss the importance of the ATT&CK® framework when responding to a security threat.
Understanding MITRE
The ATT&CK® framework is important because it helps organizations identify potential security threats that could potentially impact the digital enterprise. By using a structured approach to security incident response, security teams can better understand the nature and scope of security incidents, and they can develop a plan of action to address them. This framework provides a detailed description of the various stages of an attack and helps organizations identify what tactics, techniques, and procedures (TTPs) are being used by attackers. With this information, organizations can implement measures to prevent or detect future attacks.
ATT&CK® also provides a common language for communication between different teams within an organization. Incident response typically involves several teams, including IT, security, legal, and executive leadership. By using the MITRE ATT&CK® framework, these teams can communicate effectively, understand each other’s roles and responsibilities, and work together to address security incidents. This can help avoid confusion and streamline the incident response process.
The framework consists of several stages, including reconnaissance, initial access, execution, persistence, and exfiltration. By following this structured approach, teams can systematically identify, investigate, and contain security incidents. This helps organizations respond quickly and efficiently to security incidents, minimizing the impact on the network and reducing the risk of data breaches.
How Plixer integrates MITRE ATT&CK® into your existing workflow
Plixer gives security teams the ability to quickly identify threats on the network and see which stage those threats are in relation to the ATT&CK® framework. By mapping an incident to the ATT&CK® framework, security teams can know at a glance which playbooks they need to activate to prevent further escalation of the threat.
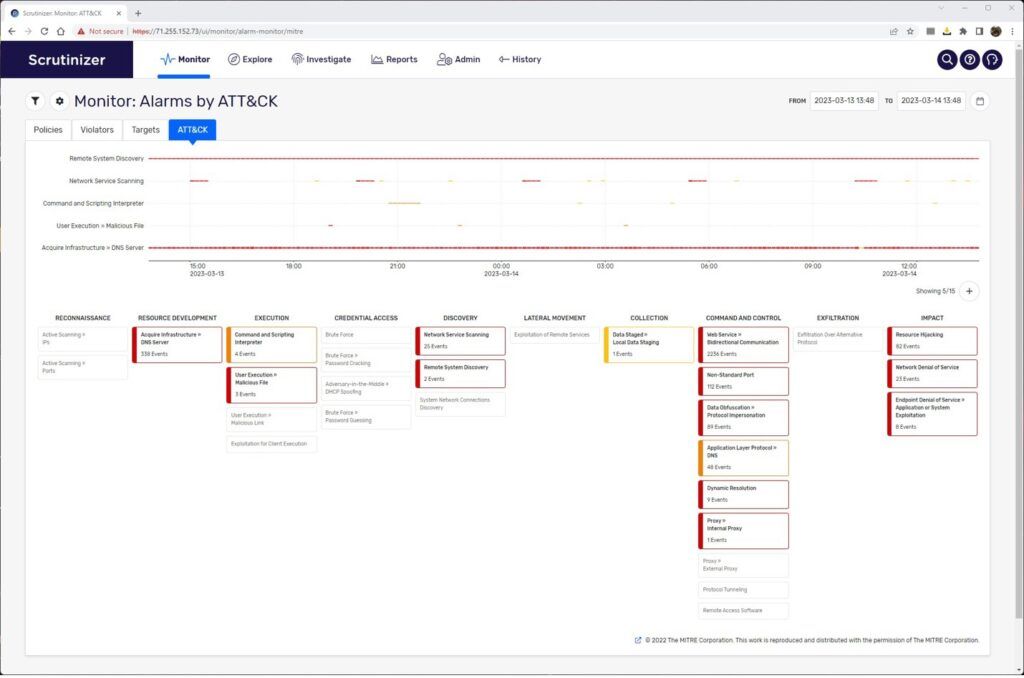
Because Plixer’s solution gives you visibility of your entire IT environment, you can also use the MITRE ATT&CK® mapping to enhance and validate your other security controls. For instance, say you have most of your in the early stages of the framework. That may be a sign that your EDR or firewalls need attention—maybe there is a misconfiguration or the system is not working as intended. Additionally, MITRE ATT&CK® mapping can help you know which system will give you the best investigative data, be it in Plixer, an IDS, or some other control. Seeing your incident volume and concentration at a glance helps your team make better decisions, faster.
If you’re considering an NDR, be sure it has MITRE ATT&CK® mapping built into the system. Having a way to quickly understand the incident will help prioritize your efforts and boost your security posture.
Request a demo today to learn more about how Plixer helps companies get the most from their MITRE ATT&CK® workflows.
