Bengway Industries is a 30 year old, 400 million dollar manufacturing company located in Western Europe. The company has 3 primary locations, each with their own Internet connection and protected by a leading firewall vendor.
NOTE: In order to share this story with the general public, the company name and contact in this case study have been altered.
The Challenge
Bengway Industries believed that they had reasonable security measures in place. Existing proactive security efforts include:
- Up to date firewalls at each location
- Anti virus is kept current on each end system
- Internet facing firewalls do not allow for incoming connections
- Flow exporting, collection and analysis was maintained as their Incident Response System
Electronic Data Theft Incident
The company’s security administrator Mark Kraft had received a call from the server team about an internal IP address (172.22 .32.46) that had failed to log onto several servers. “Often times these investigations lead to nothing, but we follow up on every one of these reports to try and ensure that nothing’s been compromised.” Said Mark “After a quick search in Scrutinizer with a few filters, I uncovered an odd cyclical pattern that I hadn’t seen before.”
Uncovering Data Exfiltration
Mark noticed that the host had been communicating with other machines internally over port 443 which isn’t typical behavior for the end system behind the IP address. More specifically, he identified a periodic upload of data to IP address 252.78.43.22 which was cause for potential concern.
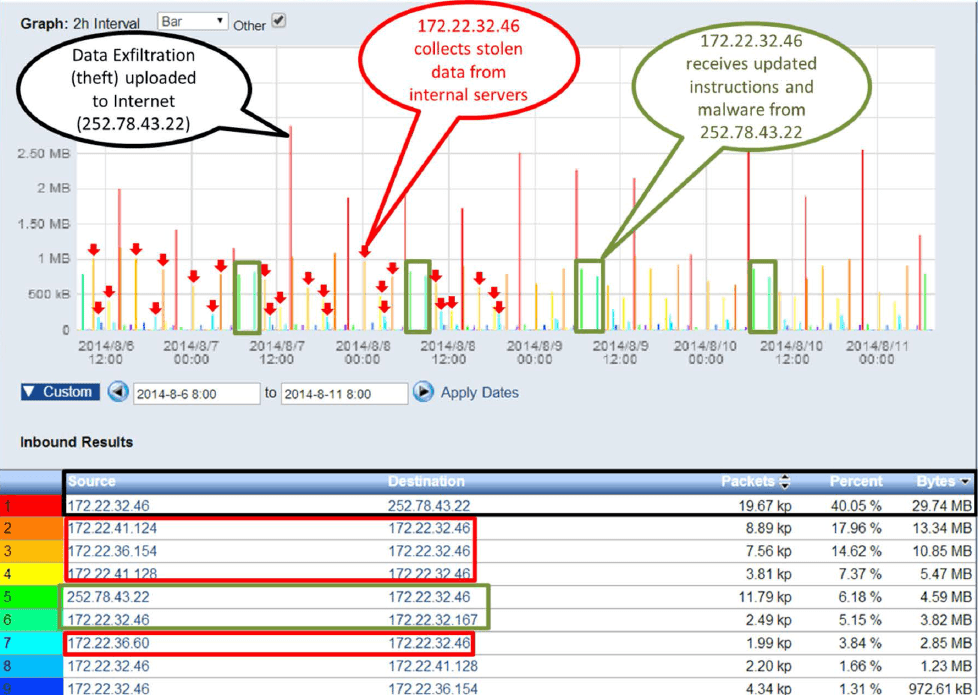
After deeper forensic review of the traffic patterns to and from 172.22.32.46 Mark was able to determine that the host was actually gathering (i.e. stealing) the data from 4 different internal hosts:
- 172.22.41.124 administration – VM server (MS Windows)
- 172.22.41.128 sales backup – VM server (MS Windows)
- 172.22.36.154 desktop – (MS Windows)
- 172.22.36.60 desktop – (MS Windows)
The above machines would upload the data over TCP 443 to 172.22.32.46 who would in turn upload it to 252.78.43 .22 . Research on the server security logs revealed that the 23 files taken were in Microsoft .docx and .xlsx format.
Additionally , there was reason to suspect that 172.22.32 .167 may also have been compromised as 172.22.32.46 was sending information to it that appeared similar in size and timing to downloads from 252 .78.43.22. Subsequent investigation took place.
Finding the Infection Source
The source of the infection was believed to have been a community email from Linkedin.com. The user click to read an article in a Word Press hosted blog. Upon visiting the web site, one of the comments in the blog loaded an infection into the computer visiting the page.
“We believe that Scrutinizer revealed all the traffic patterns related to the infiltration . Further historical reporting on the Internet host 252 .78.43 .22 did not reveal any other obvious infections however, we know what to look for and Scrutinizer is helping us monitoring for it.”
Mark is considering further investments in threat detection efforts. Immediately they are making sure that their nearly three thousand employees are aware of what happened, how it occurred as well as the dangers of the Internet especially those related to email and phishing attacks.
Scalable Incident Response System
Given only an external IP address (252.78.43 .22) that is known to be a malware command and control site Scrutinizer was able to identify:
- The internal assets (172.22.32.46) that have communicated with the malware C&C server
- Four internal servers (e.g. 172.22.41.124) that have likely had information stolen off of them and should be investigated for possible compromise
- Possible second compromised asset (172.22.32 .167) that could “go live” after the first infection detectedand cleaned up.
- The initial communications with the malware C&C server, showing when the breach started.
The Scrutinizer Incident Response System scales to meet the needs of enterprise networks by allowing for global searches across multiple distributed flow collectors all from a single interface. Each system is capable of collecting over 100,000 flows per second and the filtering and reporting allows security professionals to drill in and filter through hundreds of millions of records. Reach out to our team to setup a demonstration of our Incident Response System.