Updated: 1/6/2021
On 12/13/20, cybersecurity company FireEye published research for the SUNBURST exploit, which is affecting companies using SolarWinds software. Since the news broke, we have been experimenting with ways that Plixer’s NDR solution, Scrutinizer, can help our customers determine the impact SUNBURST may have had on their networks.
Since Scrutinizer uses network metadata, there are two data elements that stand out as good choices to use in an investigation: IP address and fully qualified domain name (FQDN).
According to the FireEye documentation, the malware uses a domain generation algorithm in order to establish connections to C2 servers and a variety of IP blocks to facilitate communication.
How can Plixer Scrutinizer help you track SUNBURST?
Unless a customer is using a next-generation flow exporter like Gigamon or Plixer FlowPro, reporting based on FQDN is off the table. For that reason, I’ll start with some IP-based examples and finish with how to substitute domains in the searches.
Using the Scrutinizer WebUI is a great starting point, but will be limited to the amount of storage the appliance has. According to the released information, SUNBURST was introduced in March 2020, which may make Scrutinizer host index a better overall candidate, since it catalogues longer time ranges. Both ways have merit, however, so we can examine each.
Using the Scrutinizer WebUI
The quickest way to visualize SUNBURST IP addresses is to create an IP group based off the subnets of interest and then perform a search for that group across all of the network devices.
Step 1: Select all devices
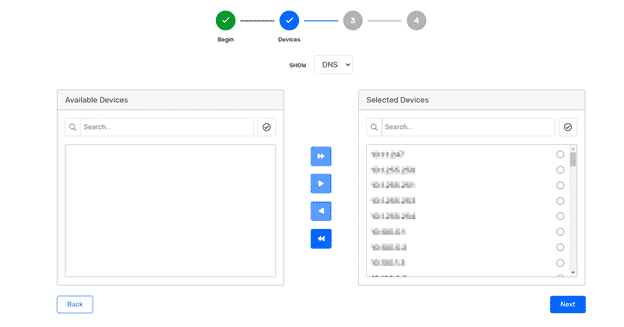
Step 2: Select report
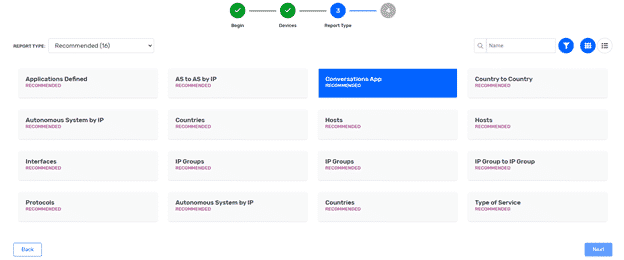
Step 3: Add IP group filter, pick the time range, and run report.
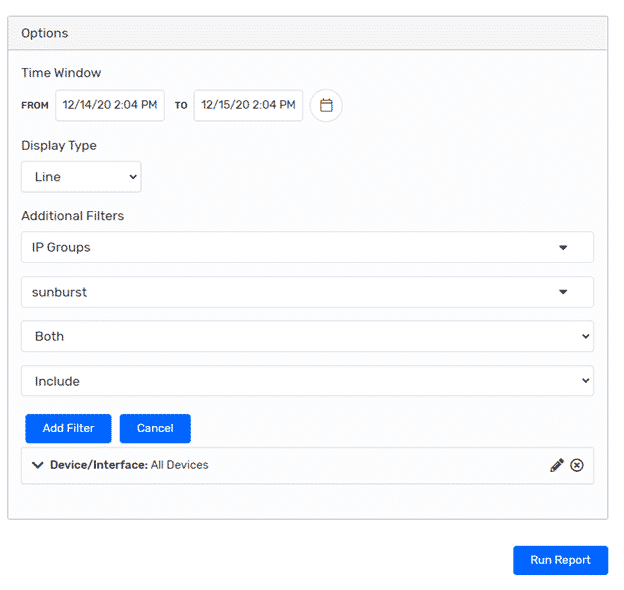
This method will present a detailed report showing each conversation that matches the IP group rule set. I prefer using host index searches instead of the WebUI because the host index will allow us to quickly see whether the suspicious IPs were on the network. If they are, we could then run reports on more granular time ranges. Let’s take a look at how that approach would differ.
Using the Scrutinizer API for host index
To make this process easier, we have created a Python script that is pre-loaded with all of the SUNBURST IP addresses and subnets. Given the number of hosts we need to search through, using the “fast” flag will ensure the host index table is the only one searched. After updating the settings.json file, you would issue the following command to perform the search:
python host_search.py fast
This script will provide two CSV files: index_detailed.csv and index_results.csv. Since I didn’t have a lab that had connections to SUNBURST IPs, I’m using a Google IP address in the example screen captures.
Index detailed
If the IP was found, it will show which device it was seen on, and at what time. This will then allow the user to pull a report specific to that criteria. Narrowing the focus helps to garner more meaningful data.
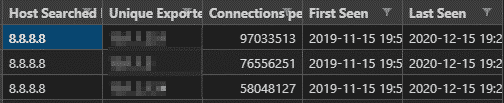
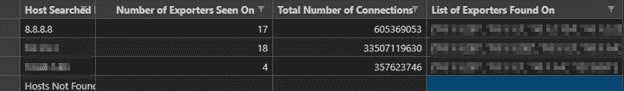
Index results
This CSV file gives an aggregate view of the total number of devices (routers, switches, firewalls, etc.) an IP was seen on, as well as the total number of connections. This spreadsheet is meant to give a snapshot of how far an IP-based threat spread throughout an organization—again allowing users to take this information and gather some more detailed reports.
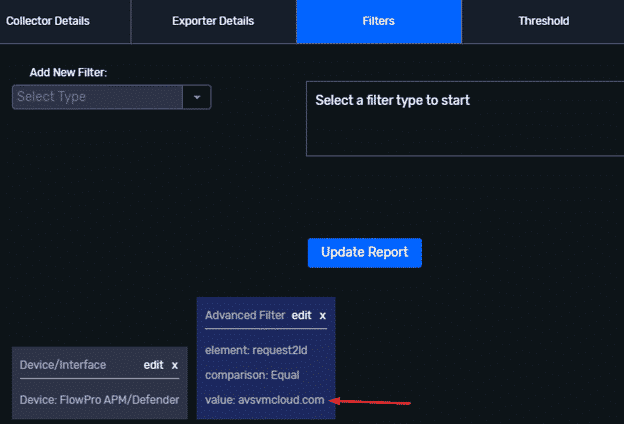
Domain-based reporting
In addition to providing IP addresses, the FQDNs supplied by FireEye can be used in a similar manner. Instead of supplying Plixer Scrutinizer with an IP group filter, we would want to apply a filter for the second-level domain name. The ability to filter on FQDNs is useful because it gets rid of some of the additional guess work that always arises from looking at IP-based data. Content delivery networks like Akamai are a great example of how IP-only searches can be obfuscated by a CDN.
Conclusion
Whether the problem is something like a radical shift to working from home or a new zero-day exploit, I consistently see network metadata as the first place people turn to to figure out how the business is affected. Taking steps ahead of time to turn on the correct devices and evaluate next-gen data formats makes the inevitable investigations all the more effective.
If there is any help I can provide in getting the script to execute or any of the reports to load, please feel free to reach out to me directly at thomas.pore@plixer.com. Due to the changing landscape around SUNBURST, we will be providing updated IOCs as they become available, so be sure to check back frequently.



