I’m often asked, “if I already have a solution to monitor this segment of the network, why do I need a solution that will overlap”? It’s a very fair question to ask, considering in most aspects of life redundancy or overlap isn’t necessarily considered good. In the case of network monitoring, I would argue overlap isn’t bad if it’s also providing correlation. With that in mind, I wanted to focus on the benefit of monitoring your wireless network traffic, and specifically having the ability to correlate this traffic across the entirety of your network.
Monitoring wireless network traffic
It should surprise no one that a large amount of network traffic today comes from your wireless environment. With IoT on an ever-increasing rise, many users don’t even physically plug into the network anymore. With this growth in wireless traffic comes the need to monitor that segment of the network for both performance reasons as well as security. Typically the monitoring tool will be vendor-specific and will solely focus on that particular network segment.
So, what’s the point of having one solution to monitor all network segments? I’m glad you asked, let’s explore!
Single pane of glass
One of the immediate benefits, and one of the most useful, is the ability to have a single pane of glass provide visibility into all network segments and follow the path of a conversation hop by hop across the network. This eliminates the need to replicate searches across multiple GUIs.
For example, I may need to find a conversation originating on the wireless network segment, just to recreate the same search on my firewall or SD-WAN monitoring solution. Simply put, you get end-to-end visibility with a single browser and a single login.
Path visibility
As I mentioned above, having path visibility is incredibly valuable when visualizing the route of a conversation or recognizing asynchronous routes.
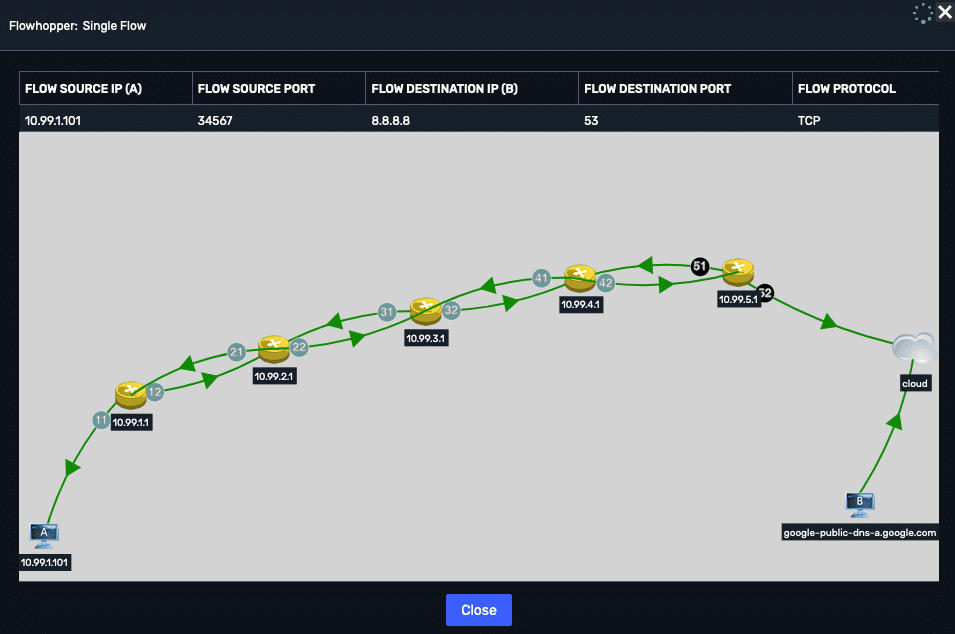
Above is a great example of visualizing the path of an individual conversation hop by hop, as it traverses the network and out through the edge.
Vendor-specific information elements
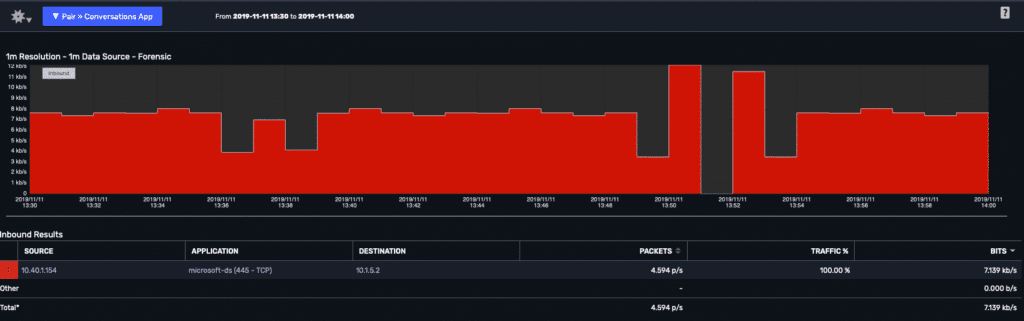
Another example of the value in correlating data across networking devices is the ability to supplement metadata with vendors that do more in-depth deep packet inspection. Here I can see from my wireless environment that I have an SMB conversation between a user on our wireless network and one of our file share servers. Within my wireless environment, I can determine the hosts involved, the timeframe of the conversation, and the application port.
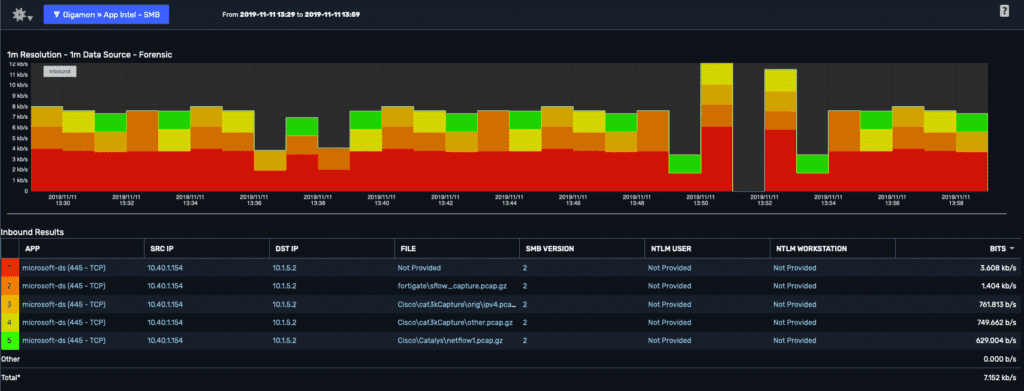
But by correlating this traffic upstream and leveraging Gigamon’s new Application Intelligence exports, I can further my understanding and see the actual file tree and filename(s) being pushed to our shares.
Correlation is KEY
I can’t stress this point enough: correlation is key. It’s imperative that we have as much information as possible at our fingertips. Equally as important, it needs to be readily available and best when it’s in a single database and can be correlated across multiple data sources.
While this blog was focused toward wireless traffic, it’s important to realize this concept can be applied universally across all network segmentations.
There are so many unique use cases that come up in this space as well. While working with this blog topic, a colleague brought up a very cool use case involving wireless visibility in a provider environment. Be sure to check back with our blogs regularly to stay informed!

