Hallmarked by the application of machine learning to network metadata, Network Detection and Response leverages advanced intelligence and integrations with response-capable solutions such as NAC and SIEM to provide incredible visibility into an organization’s network traffic. This is a stark contrast to the traditional approach of leveraging thresholds and pre-defined traffic patterns to automate network alerts. While this approach works just fine for detecting certain threats—think DDoS or SYN scans as an example—there is just so much more we can do confidently with machine learning. Let’s explore some of the more popular Network Detection and Response use cases.
Lateral movement
The first and probably most popular use case that comes to mind is lateral movement. Traditionally this would be detected with threshold values, but no threshold works for all hosts. Some hosts are chattier and by nature talk with more hosts; file servers and vulnerability scanners are common culprits. This leads to lots of exceptions and thus gaps in visibility and coverage. Introducing machine learning lets Network Detection and Response solutions account for chattier hosts. They can look at anomalous destinations and times of day on a per-host basis.
Command and Control
Detecting communications with C2 is not a new thing. In fact, it’s done the same way in many Network Detection and Response solutions, by maintaining a list of known C2 nodes and triggering when communication to one is detected. The responding side, however, is new. Instead of just generating an alert, action can be taken to stop that communication.
Data accumulation
Data movement detection was always a difficult problem to solve until we introduced machine learning. As with lateral movement, we can look for data staging anomalies.
Data exfiltration
Detecting files being transferred to Dropbox, OneDrive, or some other external site had the same challenges as data accumulation. It’s also solved in the same way with machine learning.
Detecting abnormal activity
This is the bread and butter of machine learning. Its ability to continually analyze traffic for usage that is out of the norm… and we aren’t just talking about baseline and thresholding. True unsupervised machine learning can spot these usage anomalies with little to no user tuning.
Ransomware detection
What happens when you combine abnormal activity detection with lateral movement detection and apply machine learning to it? You get really good at spotting behavior like that of ransomware. This is a great use case for Network Detection and Response.
Verifying zero-trust policies
A classic but solid use case. And perhaps one of my favorites—not just for the ability to detect policy violations, but for its ability to react and take appropriate actions.
Here is an example of what a data movement alarm (specifically data exfiltration) looks like in Plixer Scrutinizer:
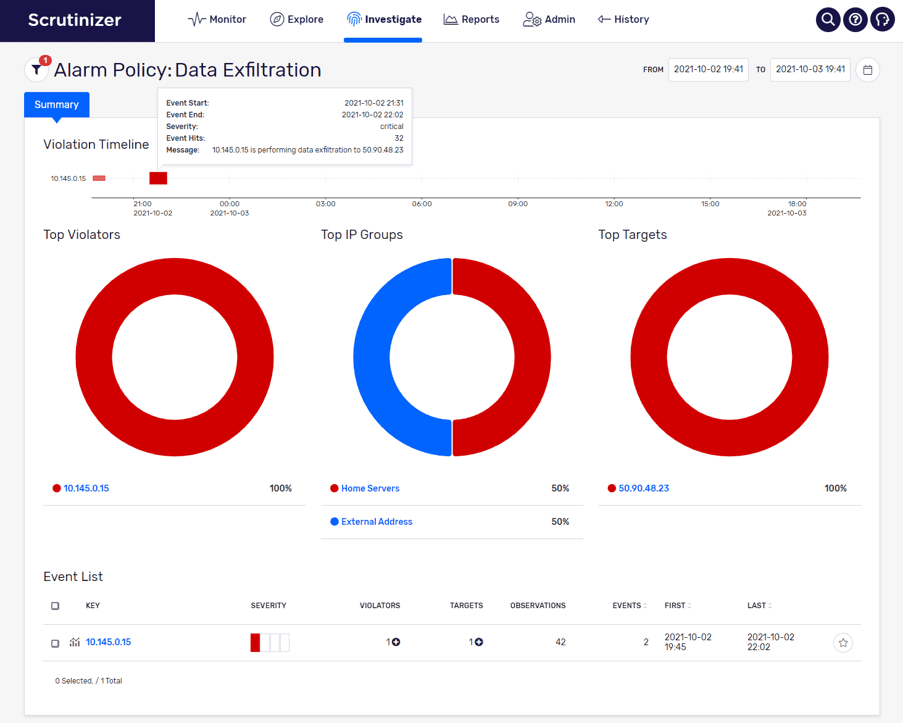
You can see from this screenshot that a server (10.145.0.15) sent an anomalous bit of data to the external host (50.90.48.23) over a 31-minute period. We can click on the small graph symbol at the bottom left of the page to see additional details and data involved in the exfiltration.
If you want to see how we address any of these use cases, feel free to reach out and schedule a demo!



