What is STIX/TAXII?
STIX stands for Structured Threat Information Expression, which is an open-source language and serialization format used in sharing threat intelligence. Think of it as the vehicle for containing the threat information. Threat intelligence is communicated as objects and is detailed or as brief as the creator would like. TAXII stands for Trusted Automated Exchange of Indicator Information and is an application protocol that uses HTTPS/HTTP to enable communication. Think of this as the highway for STIX to travel on.
These are format standards that enable an easy way to share cyberthreat information throughout the community. They are also used to share threat intelligence between various security tools and teams internally and with consistency. Different tools can apply different information that is packaged by these feeds to keep your software up to date or your network protected from bad actors. Oasis Open, which maintains the STIX/TAXII standards, has a nice visualization of the information contained in a STIX-formatted threat report.
Where does the data for STIX/TAXII come from?
One of the key principles and advantages of the STIX/TAXII paradigm is the sourcing of its data. Many feeds go the traditional route of using automated honey pots or API integration to VirusTotal and other malware sandboxing services to create actionable threat intelligence. These are all great sources, but one of the advantages to using STIX/TAXII is the ability to crowdsource this information. The community can follow the standards and submit threat information that can then ripple through the community to provide protection to others as soon as they encounter new threats.
These standards do not have to be applied simply to open data. Highly sensitive networks that encounter targeted attacks from threat actors can maintain their own STIX/TAXII feeds that can be updated internally and applied throughout their network. This also makes it possible to apply the STIX/TAXII paradigm to networks without internet access, as long as you supply the feeds with enough information to continue to be useful.
The content of STIX
The STIX standard provides an object-based way to organize your threat intelligence. This makes it easy to use the information you would need to make decisions to protect your network. These objects are represented in relationships to other objects, giving you a precise understanding of the threat you are investigating. For example, here is a STIX campaign object represented in JSON provided by Oasis Open:
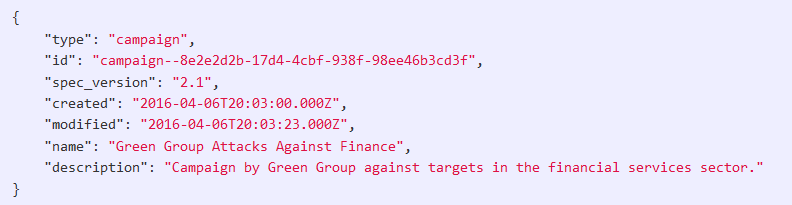
This Campaign object could be bundled with other objects in relation to it. For instance, maybe there is a certain malware that has been associated with this campaign and we want to monitor for its hash signature. Other times, domains for command and control servers or URLs of phishing sites are provided. There are currently 18 STIX objects available to classify threat information and these can be bundled together or pointed to each other, indicating certain types of relationships to help describe threats.
List of feeds
Many feeds require licensing or product purchasing, but there are some free feeds out there as well. This is not a comprehensive list but may help you get started in the right direction:
- OTX Alienvault: Requires signing up and acquiring an API key
- Limo from Anomali: Free with guest/guest credentials
- HailaTaxii: Allows free and anonymous connection
- PickupStix: Free with guest/guest credentials
- ThreatConnect: Demo only
Check out Plixer’s new product, Plixer Security Intelligence, which integrates with STIX/TAXII, so you can be alerted and make informed decisions based on the most up-to-date threat intelligence.
