Phishing attempts have been showing up a lot in the news lately and scammers are getting smarter. What can we do? What shouldn’t we do?

Go phish
The other day, a friend called me because he got three emails from a weird address:
- The first had one of his website passwords in the subject
- The second asked him to verify his account
- The third claimed to have webcam footage of him, and demanded he pay money, “or else”
Thankfully, I was able to walk him through what needed to be done: delete the emails, run a virus scan, and change his passwords.
I didn’t think much of this—phishing happens—until I got to work and had an email from Microsoft Outlook claiming I had several unread messages in my spam filter and needed to follow a link to view them. It looked official enough, but I noticed the link in the email contained a bunch of letters and numbers before the “.com” and the landing page asked which email provider I use. If this really was coming from Outlook, why are they asking me who my email provider is? Something seemed… phishy.
What is phishing and what not to do
A phishing attempt is when a bad actor sends you an email asking you to verify information. That information can be your username and password for a website, or it could be your bank information or social security number.
Bad actors do whatever they can to make the look as authentic as possible, which can make it very hard to determine whether or not it’s the real deal. Here’s what you can do to protect yourself should you get an email that looks suspicious:
- If there is a hyperlink in the email, hover your mouse over it and do not click it! If the link contains a bunch of gibberish that makes no sense, chances are it’s not real.
- If the email says that you are required to input personal information, don’t do it. If it looks legitimate, call or email customer service from the company that the email came from. Ask them if they sent out an email asking for information. Most companies will explicitly state that they will never ask for personal information, especially over email. For example, if Netflix emails you asking to update payment information, call their customer service first.
- If the email looks sketchy from the get-go, don’t even open it. Delete it right away. Some emails contain a 1×1 pixel image that tells the bad actors that you’ve opened the email.
These are just some simple steps, but you can learn more by looking at the Federal Trade Commission website and reading their tips on how to avoid and recognize attempts.
My last bit of advice: if this happens at work, forward the email to your security team. Hopefully, they use Scrutinizer and our FlowPro Defender.

How Scrutinizer and FlowPro can help
By pairing up Scrutinizer and FlowPro Defender, you can track down where your data will go if you click the links. Scrutinizer can show you IPs and conversations from one IP to another, as well as source and destination countries. On the other hand, FlowPro Defender can show you NXDOMAIN (those gibberish URLs I mentioned before), FQDN reports, and reports on DNS requests.
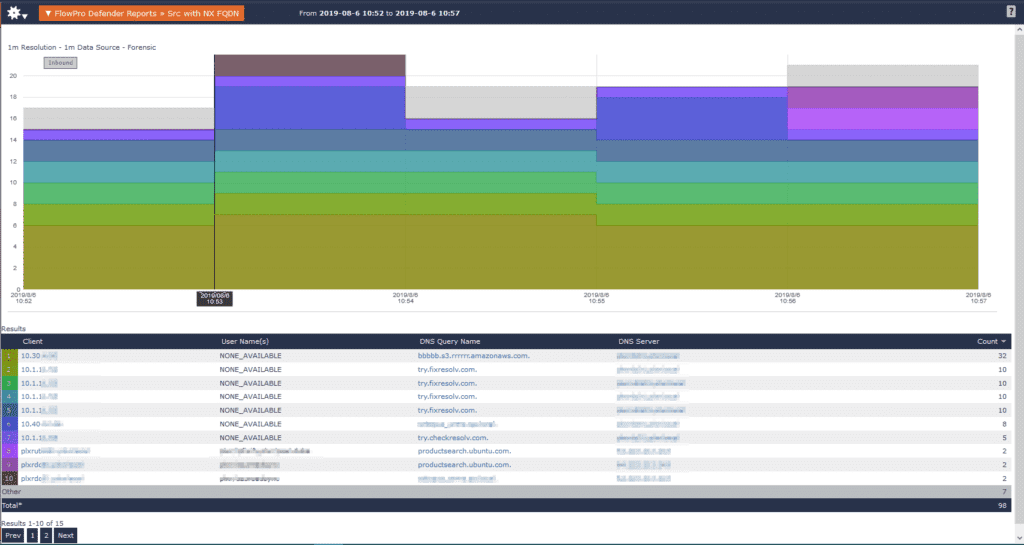
Once you know the IPs involved, you can prevent future issues by blocking them on your network. For example, in the image below I have my top ten IP sources and the NXDOMAINs they are reaching out to.
Remember, if you need help setting these up or have any questions for us, give us a call!


