Plixer One Expands Cloud reach and Supercharges AI and UX
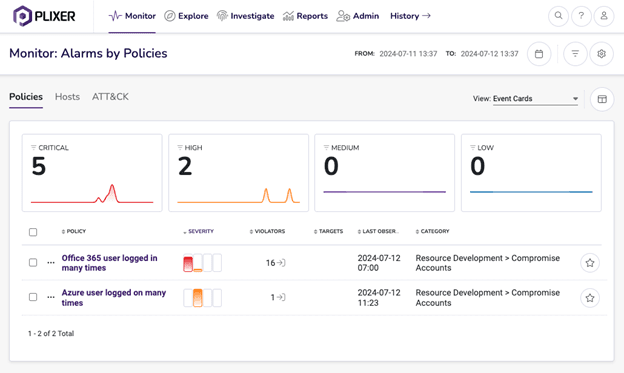
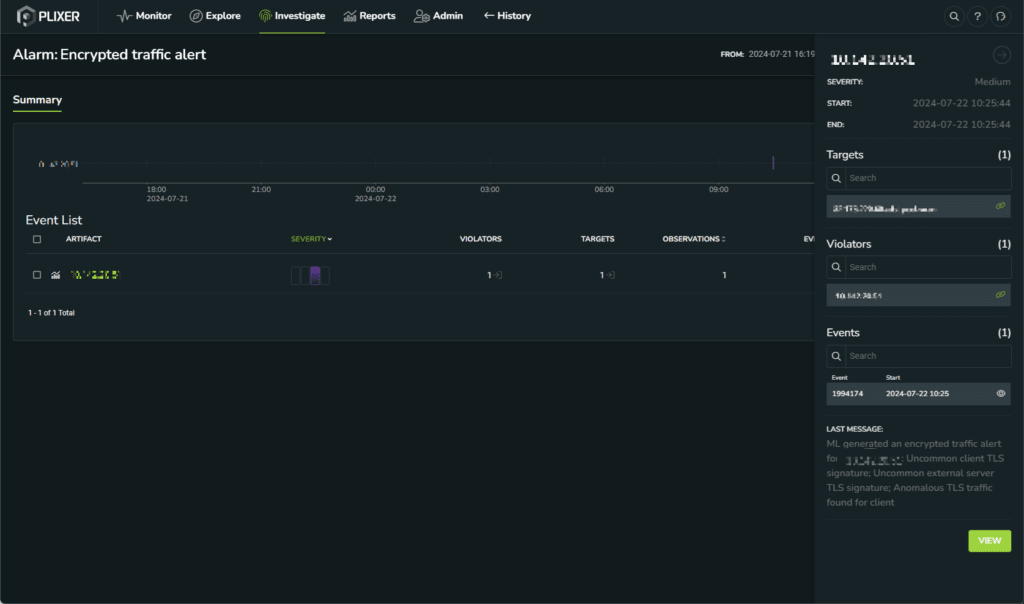
Plixer is excited to announce the latest release of Plixer One, now delivering extended support for Oracle Cloud Infrastructure (OCI) and Google Cloud Platform (GCP). This update empowers enterprises with broader cloud visibility, optimized user experience, and intelligent automation ...
Continue Reading