NetFlow Security Analytics
Detecting threats and intrusions on your network is an ongoing, evolving process/battle. Keeping up with NetFlow Security Analytics is something we strive for with each rendition of Scrutinizer. Our algorithms were engineered to effectively identify security breaches, suspicious behavior and provide timely incident response. Read below for some of our latest additions.
New Correlation Algorithms
Flow Analytics™ algorithms demonstrate Plixer’s cyber threat correlation capability. Correlation of multiple network behaviors over a long time period provides detection systems with more information allowing for a higher accuracy with fewer false positive alarms. The new algorithms are:
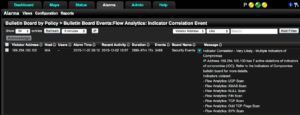
- Indicator Correlation Event
This algorithm escalates multiple IOCs and security events for a single host to a new alarm on the security event BB. While a single IOC may be indicative of malware, it is much more likely to be a real security concern if there are multiple indicators. By default, this algorithm correlates multiple IOCs along with any events posted to the Security Event BB and issues an alarm for any host that has three or more entries in the IOC and Security Event bulletin boards. Each of the contributing algorithms will be listed in the alarm message:
- Malware Domain Communications
This algorithm combines the Domain Reputation algorithm with communications detected going to the IP address that was resolved.
Scrutinizer and FlowPro Defender have detected the following sequence of events:
- FlowPro Defender contains a list, updated every 10 minutes, of over 700,000 known malware domains created by forensic analysis of the actual malware software. These are very high confidence domains.
- FlowPro Defender monitors all of the DNS resolution requests, and generates an IOC alert on detection of a match with a malware domain and saves the resolved “Malware IP Address”. This only rates an “IOC” as a browser may “pre-fetch”, or resolve address, for all of the links on a web page to make browsing faster. However, as yet, no connection to the malware site has been made.
- Scrutinizer then examines all flows for any communications with the “Malware IP Address” resolved by Defender. On detection of any flows to or from that address, a connection to the malware site has been established, and a Malware Domain Communication alert is issued.
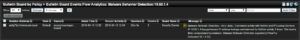
- Malware Behavior Detection
This specific alarm is correlating IP address lookups activity, which is commonly performed by malware shortly after the initial compromise, with the detection of the BotNet alarm or with a Domain Reputation alert. In other words, this algorithm looks for the following correlation:
- IP address lookup combined with a Domain Reputation trigger
- IP address lookup combined with a BotNet trigger
When either of the two events is detected, this algorithm is triggers as this behavior is a very strong indicator of a compromised asset.
New Bulletin Boards
Our slew of analytics is now posted to one of three Bulletin Boards (BB), depending on their importance and likelihood that a host has been compromised. The different bulletin boards are:
- Security Events
The algorithms that post to the Security Events bulletin board are highly indicative that a host is compromised. You should monitor and investigate any events posted to this bulletin board. The following algorithms are posted to the Security Events BB by default:
BotNet Detection • DDoS Detection • DNS Command and Control Detection • DNS Data Leak • Indicator Correlation Event • Malware Behavior Detection • Malware Domain Communications • Host Reputation (Tor, Blackhole, Malware C&C Server, and user defined)
- Indicators of Compromise (IOC)
The algorithms that post to the IOC bulletin board are those that indicate possible malware activity, but are not necessarily a security event alarm.
This is a bulletin board that you may want to periodically review to look for recent changes that may be of concern. If multiple IOCs are associated with a single host, these may generate an “Indicator Correlation Event” alarm that is posted to the Security Event BB. This is discussed in more detail below. The following algorithms are posted to the IOC Events BB by default:
Breach Attempt Detection • DNS Hits • ICMP Port Unreachable • ICMP Destination Unreachable • Denied Flows • Denied Flows ASA • Domain Reputation • FIN Scan • NULL Scan • Odd TCP Flags Scan • RST/ACK Scan • SYN Scan • TCP Scan • UDP Scan • XMAS Scan
- Policy Events
Algorithms that post to this bulletin board are those that detect network traffic that generally have no direct security implications, but may violate your network policy.
The following algorithms are posted to the Policy Events BB by default:
Excessive Jitter • Multicast Violations • IP Address Violation • P2P Detection
Note: you may edit the policy for any algorithm to change the Bulletin Board from the default settings.
Additional Distributed Reflection Denial of Service (DrDoS) Detections
Scrutinizer now detects eight DrDoS attacks:
DNS • NTP • SNMP • SSDP • CharGen • NetBIOS Name Server • RPC Portmap • Sentinel • Quote of the Day
You also have the option to enable or disable a specific reflection attack via Admin > Settings > Flow Analytics Configuration > DDoS settings:
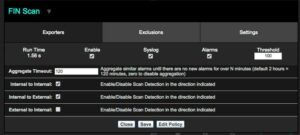
New Controlling Scan Algorithm “Scan Direction”
All of Scrutinizer’s scan algorithms are looking for “internal to internal” and “internal to external” scanning activity, by default. Now, you now have the option to control which scanning directions the different algorithms look for, including the addition of “external to internal”, which would normally be used to monitor public facing IP addresses listed in an IP Group. Within each of the scanning algorithms, the settings screen provides a directional control option:
Hope this aids your NetFlow Security Analytics, by improving detection and correlating all the different violations across the network.
Please contact out team to help configure these new additions, along with any other of your network monitoring needs.