As we navigate through 2024, the cybersecurity landscape is increasingly dominated by stealth and sophistication. The recent CrowdStrike Global Threat Report highlights a dramatic rise in covert activities, including data theft, cloud breaches, and malware-free attacks. This trend underscores the evolving tactics of cyber adversaries who are becoming more adept at using valid credentials and legitimate tools, making detection significantly more challenging for organizations.
The Rise of Generative AI-Driven Cyber Threats
Generative AI is transforming the way malicious actors carry out attacks. Hackers now use AI to craft more convincing phishing attempts, automate malware development, and bypass identity controls through sophisticated tactics like SIM-swapping, MFA circumvention, and API key exploitation. With these tools, adversaries are not only evading traditional security measures but also launching identity-based attacks with alarming precision.
These developments emphasize the need for behavior-based analytics to monitor and detect anomalies across networks. As attackers mimic legitimate users, it is no longer enough to rely on static security methods—security teams need deeper insights into user behavior and entity interactions to pinpoint suspicious activities.
The Ongoing Threat of Ransomware and Data Breaches
Ransomware remains a serious concern, with attacks like the breach at the Superior Court of Los Angeles County serving as a stark reminder of the vulnerabilities across sectors. According to Gartner, ransomware and similar cyberattacks are expected to cause $10.5 trillion USD in damages annually by 2025.
Adding to the urgency, 81% of organizations reported experiencing at least 25 cybersecurity incidents within the last 12 months. As these threats grow more frequent and damaging, security teams need solutions that provide comprehensive visibility and facilitate fast, efficient responses.
Proactive Threat Detection Through Behavioral Insights
In today’s rapidly evolving threat landscape, analyzing behavioral patterns across users and devices is essential. Behavior-based analytics allow organizations to detect anomalies that indicate insider threats, compromised accounts, or unauthorized access—threats that would otherwise evade detection. Security teams can correlate behavioral data with network activity to respond faster and more effectively to potential threats.
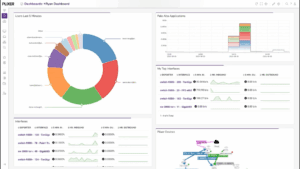
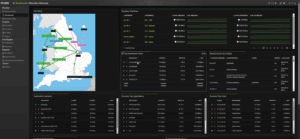
Plixer One is a network observability and defense platform designed to deliver actionable insights by capturing and analyzing behavioral patterns in real-time. By monitoring authentications and other network activities, the platform helps organizations identify suspicious behavior across on-prem and cloud infrastructures.
The ability to detect abnormal activity—such as excessive authentications, inconsistent geographic logins, or new privileged accounts—provides security teams with critical insights to mitigate risks before they escalate. This identity monitoring also aligns with Zero Trust principles, ensuring continuous validation of every user and device interaction within the network.
Network Observability for SecOps and NetOps Collaboration
The Plixer One platform bridges the gap between NetOps and SecOps by unifying network data and behavioral insights into a single, actionable view. This integration empowers security teams to monitor, detect, and respond to threats across the entire network, ensuring faster incident response.
By combining flow-based monitoring with AI and behavior analytics, security teams gain complete visibility into authentication activity and user behavior. This comprehensive view enables them to identify indicators of compromise—such as data exfiltration or lateral movement—and take immediate action.
Stay Ahead of Cyber Threats in 2024 and Beyond
With cyber threats becoming more elusive, organizations need tools that offer real-time visibility to stay one step ahead. The observability and defense capabilities found in Plxier provides the advanced monitoring needed to detect suspicious activity early and respond effectively.
🔍 Want to learn more?
Stay ahead of the latest threats—read our blog on enhancing security with behavior analytics to discover how behavior-based monitoring can safeguard your organization. [Read Now]
Let’s navigate these rising threats together—contact us today to learn how Plixer One provides unmatched network observability and defense to help better protect your business and empower your security and network teams.