Author: Ryan Mellmer, Plixer Software Engineer
The world is currently in an AI (Artificial Intelligence) revolution. AI is everywhere today; in the news, in our social media feeds, and increasingly in our daily workflows. Many companies are making a lot of claims about AI and the exciting new benefits it provides, but how much of this is true, and how much is just hype and buzzwords? At Plixer, we are continuously researching new technologies to incorporate into our products to better protect our customers, including AI. However, is AI the best tool to solve every large data analysis problem? Or are more traditional machine learning (ML) methods still superior for some applications? This is a critical question to ask, especially in the middle of a hype-cycle that we currently find ourselves in. In this blog article we will dive into where ML still provides value in network operations and network security in 2024 and beyond.
Defining Terms
Before we begin, we need to define some terms.
First, what do we mean by AI? Turns out AI, until very recently, meant just any computer system that exhibits intelligence and learning like that of humans. Using this definition of AI, it is obvious that traditional ML applications and algorithms fit the criteria, because they train a machine to think autonomously. See the following AI hierarchy:
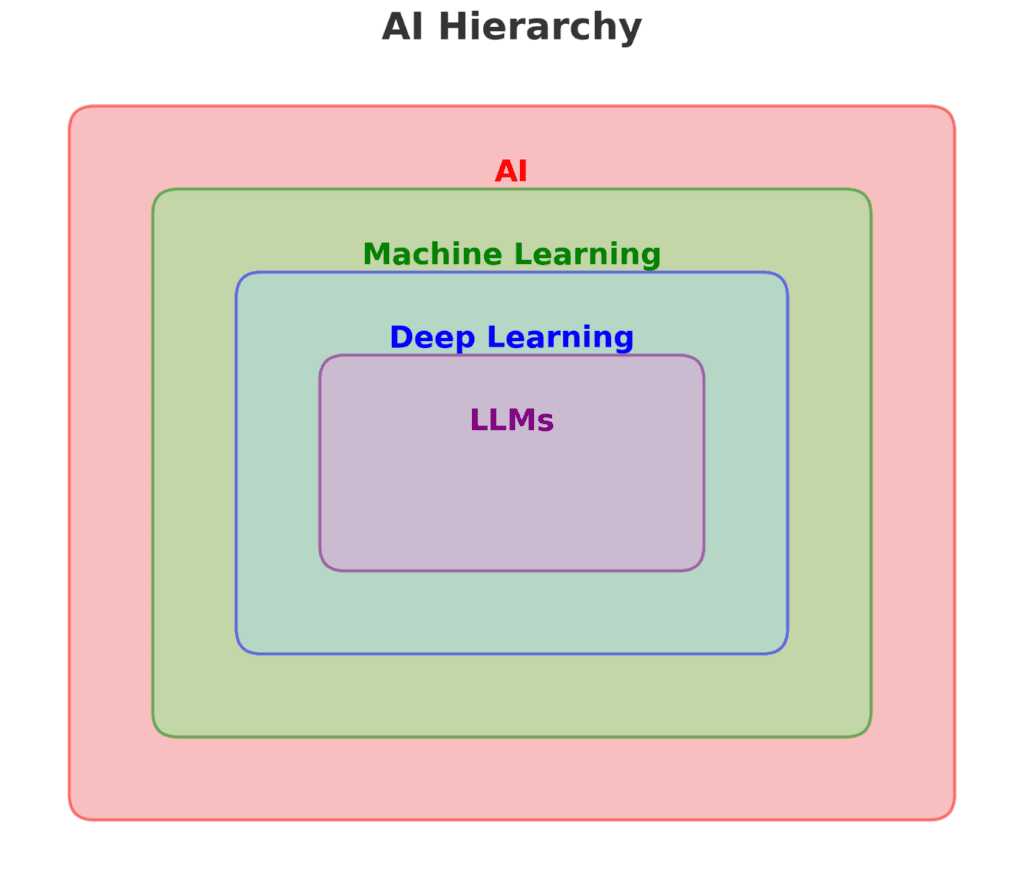
According to this chart, things like LLMs (Large Language Models) and Deep Learning fall under the umbrella of ML, which means any program that “learns” by itself without a human manually providing the logic with which the machine makes decisions. However, in 2024 when people refer to “AI”, they often mean things in the innermost quadrant, including generative AI such as LLMs (GPT-4, Llama, etc.) and Image Generation models (Stable Diffusion). The cultural definition of AI is beginning to shift (regardless of how incorrect it may be), we will assume AI means LLMs and other generative AI models in the middle of the AI hierarchy for the remainder of this article.
LLMs are obviously immensely powerful tools that continue to enable developers to solve problems that were not possible even this time last year. AI has already revolutionized several fields with its ability to understand patterns and predict next steps for complex tasks and has led to a rapid adoption of LLMs across various domains, increasingly in security applications. But does that mean that LLMs are now the only useful AI algorithm to reach for?
The Pitfalls of LLMs and the Value of Traditional ML Algorithms
Power Efficiency
LLMs are extremely powerful. But as we are quickly realizing, this new AI superpower comes at a significant cost in terms of the electricity used to keep them running. LLMs are extremely power hungry and require beefy GPUs not just for training, but inference as well. Contrast this to traditional ML algorithms like XGBoost (gradient boosted trees), and K-means clustering (unsupervised ML), which can be ran on modest CPUs and require significantly fewer resources to obtain similar inference speeds. This means traditional ML comes with significant cost savings to analyze the large datasets found in network security applications.
Domain-Specific Training
Training ML models to detect and classify domain-specific traffic is much easier than training LLMs to do the same thing. For example, if you wanted to use a LLM to detect anomalies in your organization’s very unique network traffic, you’d either need to only feed the LLM with a limited amount of historical network traffic (to stay within the context length limitations of the model), or fine-tune the LLM with your data which is a costly endeavor for the reasons we discussed above.
When we compare this to using traditional unsupervised ML to baseline a specific network’s trends and find anomalies that lie outside the norm, we find clustering algorithms are much better suited for the task at hand and allow us to model against extremely large historical datasets at a low cost of compute. This is exactly the approach we use with the Plixer One Security platform to generate thousands of models unique to a customer’s network to baseline and detect anomalies efficiently and effectively.
An Example Use-Case
At Plixer, we have many test scenarios we use to emulate attacks that are commonly seen in customer environments. For example, the following shows a host that reached out to a malicious HTTP server and got infected with a banking trojan malware. Plixer’s supervised Machine Learning platform detected this malware and generated various alerts:
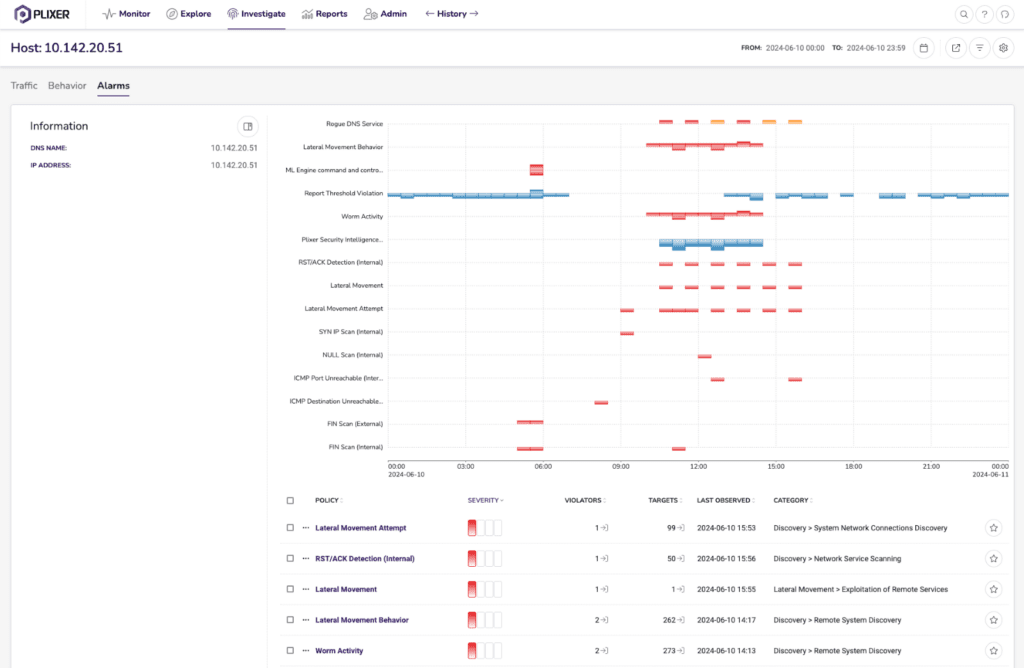
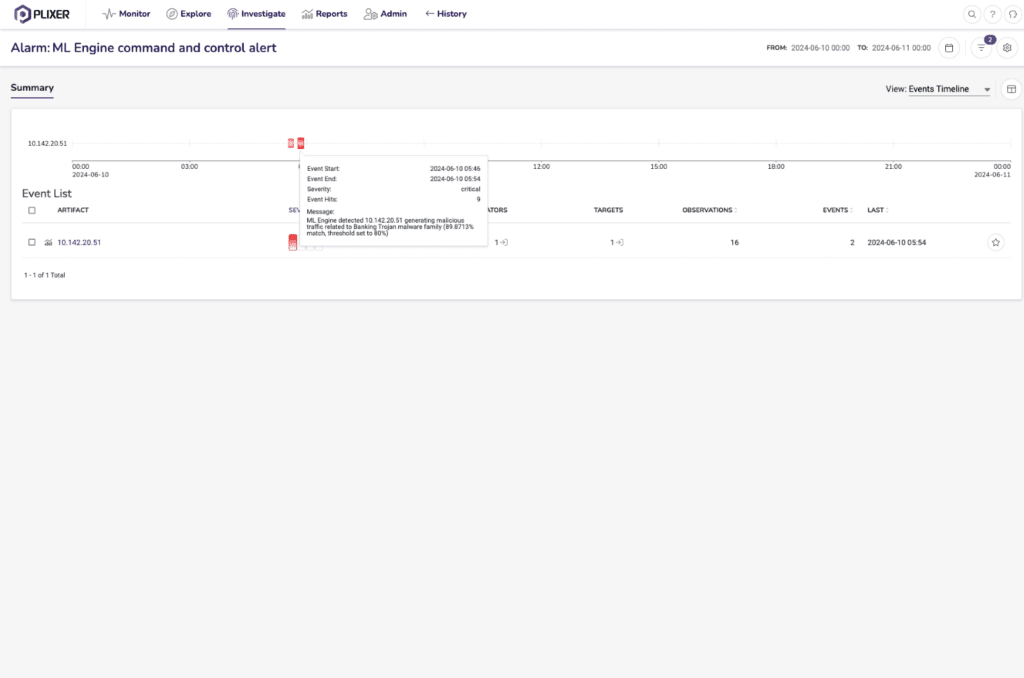
In the timeline view for this host, we can see that it reached out to a known malicious host, then was infected with a banking trojan that started exhibiting command and control behaviors (detected via Plixer ML Malware models) and began its reconnaissance step. Recon was detected through various alerts, some deterministic (like SYN IP scans), and some ML based detections like lateral movement and worm activity alerts as the infected host scanned the network for other machines to infect.
Further diving into the MITRE Attack framework view within Plixer Scrutinizer, we can clearly see the various detections, both ML and non-ML, all grouped by their MITRE category. This level of detail and being able to see the progression of a threat across your network as a function of time is invaluable for threat hunting and auditing.
Balancing Innovation with Practicality
While the draw of the latest AI advancements is strong, and largely for good reason (the tech is very impressive and exciting), it is important to balance innovation with practicality. The “latest and greatest” AI models are not always the best fit for every application, and network security is one such area where traditional ML algorithms continue to shine. By leveraging the strengths of traditional ML, network security professionals can achieve robust, efficient, and interpretable solutions that are well-suited to the demands of their business. At Plixer, we are always looking for ways to innovate that provide maximum value for our customers while still balancing cost and efficiency. To learn more about how Plixer One can enhance your network security, visit our Plixer One Security page. Explore our cutting-edge solutions and see how we can help you achieve a secure, efficient, and resilient network.



