Increasingly complex cyber threats are pushing SOC analysts to ‘up their game’. It has become critical to quickly understand how an attacker has gained access, what techniques were used to breach your systems, where they have been, and what they have done. Capabilities such as Incident Correlation and leveraging the MITRE ATT&CK® framework are being used to improve the SOC investigative processes.
In support of these objectives, Plixer has expanded its solution capabilities to improve security analyst productivity and effectiveness. These capabilities can be used individually or in combination to provide additional context to threat detections.
MITRE ATT&CK® for Enterprise support
The MITRE ATT&CK® framework has become the de-facto standard for communicating across SecOps teams during incident investigations. This framework provides a knowledge base of tactics and techniques that threat actors employ to achieve their goals. Use of security tools that leverage the MITRE ATT&CK framework provides a structured way to investigate an incident, drive faster investigations, and promote collaboration and SecOps efficiencies. This can also help to prioritize security incidents.
Plixer has engineered MITRE ATT&CK® for Enterprise tagging (identifying tactics/techniques/sub-techniques) into its alarm policies. Where in the past this was a manual process for customers, reliant heavily on the knowledge of the security analyst, Plixer now delivers specific MITRE ATT&CK® information natively in the UI. In the alarm monitor screenshot below, the MITRE ATT&CK® categorization is displayed on the right side of the screen, next to the corresponding alarm.
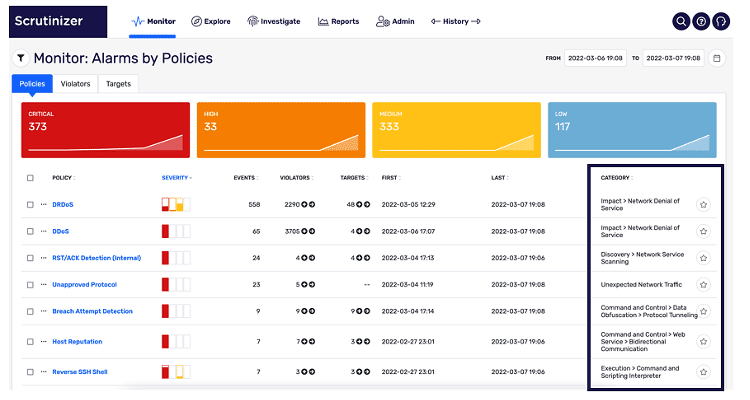
Additional capabilities around the MITRE ATT&CK® framework will be provided in upcoming releases.
Security Incident Correlation
The MITRE ATT&CK® framework helps guide an analyst on what to investigate next. For example, if an analyst sees a Discovery technique being used, the analyst may want to look for indications of Lateral Movement on that same machine – or look for Credential Access or Execution to understand how the attacker got onto the machine in the first place. Security incident correlation automates the process of analyzing events and identifying relationships between them to establish the scope of the larger incident.
An event is any piece of data that provides insight about a state change in the infrastructure, such as a user login. Most of these events are normal and benign, but some will signify a potential security issue. Because a typical enterprise may process thousands of events each day, correlating all of them to determine which are truly relevant represents a significant challenge for security teams.
Plixer has expanded its Incident Correlation capabilities to assist the analyst with connecting related events into an incident. When an alarm triggers, Plixer will automatically invoke Incident Correlation algorithms. This uses automated forensics to unravel, correlate, and group additional events which can be associated with this alarm, thus leveraging an identifiable meaningful pattern (or chain of events) pertaining to the broader security incident. Timeline visualization of the aggregated set of events that comprise this incident is also provided, including drill-down capabilities.
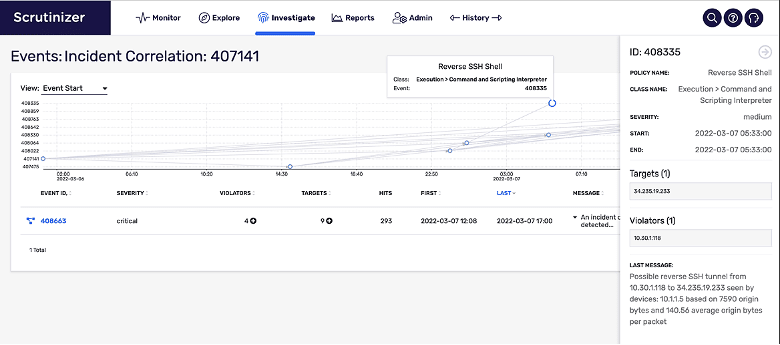
By delivering this incident focused view, security analysts gain a comprehensive, unified understanding that would be difficult to achieve from investigating isolated individual security events – in turn, driving an informed decision on where to go next to respond and investigate. In addition to improved analyst productivity, use of Incident Correlation reduces alert ‘noise’ and increases overall SecOps team efficiency.
In summary
Combining MITRE ATT&CK® support and enhanced Incident Correlation capabilities allows Plixer NDR platform customers to better prepare and respond to advanced cyber attacks. Both features leverage Plixer’s multifaceted detection methods to reduce MTTD/MTTR of security incidents.
Interested in learning more? Read our Network Detection and Response platform technical whitepaper or request a demo today.

