This blog will go over how to use some of the features in Plixer Scrutinizer v19.0, such as the host index and IP groups functionality, to quickly define your endpoints and reduce the time it takes to find suspicious hosts. Recently we have seen an uptick in customers looking to use this functionality to its fullest to help speed up incident response.
Endpoint monitoring and visibility
If you’ve read any of our other blogs, I’m sure you are familiar with how powerful NetFlow/IPFIX data can be in tracking down network issues such as overutilized circuits, anomalous hosts and lateral movements. However, there’s one feature that can be especially helpful with all of the above use cases, plus with many more.
IP groups is a feature that allows you to input specific IPs/subnets or IP ranges into a logical group, allowing you to quickly search and filter based on these parameters. Another big benefit is that if you already use an IPAM solution like Infoblox or BlueCat, we can easily import this data.
Starting under Admin > Definitions > IP Groups, we will get a window that allows us to punch in the different hosts. In this example, I will identify a couple of suspicious servers that I want to monitor communication from. Given recent headlines, I find this example of monitoring endpoints to be top-of-mind for most of you reading this.
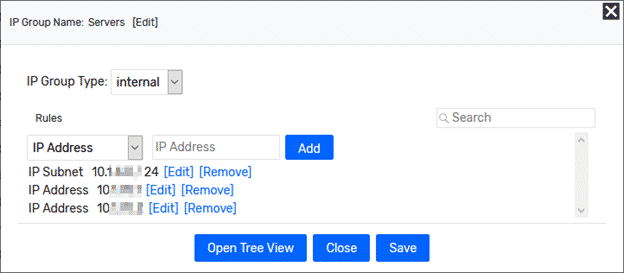
Monitoring the newly created group
Using this new group, we can quickly run through some entity views to get an understanding of how these devices communicate on the network.
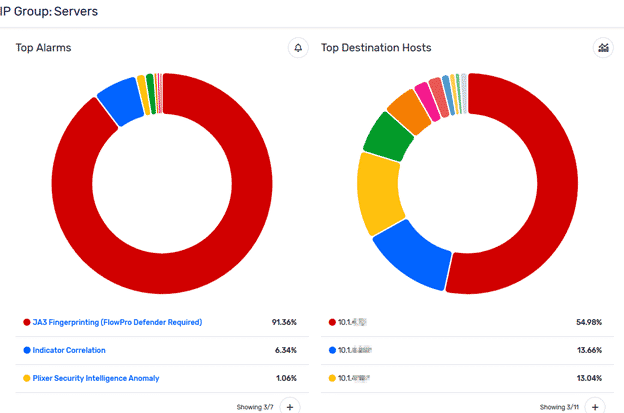
These new views within Plixer Scrutinizer 19.0 quickly give you a dashboard-style view for the group in question, which can help you identify any security events, top applications, and top hosts involved in that view. I use this all the time to quickly gauge how busy a particular group is and what they are up to from a single click rather than a bunch of reports. We also have a variety of views available for other items such as countries, applications, and hosts, but that is a topic for another blog.
Using the host index search
Host index is a feature that has been in the product for a while, but has been revamped for v19.0. In this version we have added more functionality to allow you to search through the index using two IPs (Host to Host). You can use this feature any time you are doing incident response work and need to quickly verify that communication has occurred between two hosts.
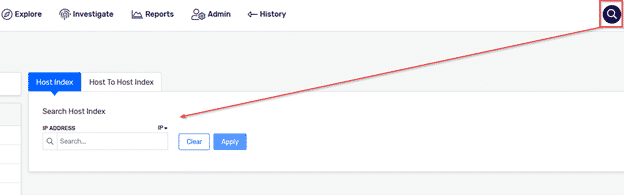
This feature was designed for incident response teams to quickly confirm or deny whether traffic occurred on the network that might require further investigation. The most common use case I see for this is to take a server and a potential IOC they might have reached out to and use host index to quickly verify if communication has ever been observed.
Incident response workflows
Hopefully, these new features will help you out during your incident response investigations. These are just a few of the new tools v19 provides to help speed up the search for suspicious hosts. If you want to take advantage of these new workflows, feel free to reach out to our team or check out our other blogs for more ideas.