Author: Reilly Collins, Plixer Software Engineer
In a threat landscape that is constantly evolving, authentication-based incidents continue to be one of the biggest concerns for cybersecurity professionals today. Insider threats, brute force attacks, compromised accounts – how can security teams stay one step ahead?
As sophisticated threat actors execute complex attacks across multiple users, IT devices, and IP addresses it is imperative that SecOps implement more effective means to analyze user and entity behavior activities and enhance detections of cyber threats that hide behind trusted users and devices to evade security tools. The complexity of these attacks often makes it challenging for security teams to identify threats like insider activity, compromised accounts, and unauthorized access. In fact, 65% of organizations report insider threats as the hardest to detect, underscoring the need for advanced threat detection capabilities. User and Entity Behavior Analytics (UEBA) provides the critical insights needed to identify these hidden dangers by monitoring behavioral patterns across users and entities, allowing security teams to spot anomalies and act swiftly to mitigate risks. In this blog, we’ll explore how Plixer’s UEBA can help bolster your defenses against threats lurking within your own infrastructure.
User and Entity Behavior Analytics (UEBA) with Plixer One lets you see understand and address suspicious user and endpoint behavior that is indicative of a security threat. This tool enhances an organization’s security posture by detecting anomalies in user and entity behavior, then providing actionable insights for your security team to mitigate these risks. Plixer’s UEBA solution is non-intrusive and comprehensive, identifying user- and entity-based security risks in real time. With data from both on-prem and cloud infrastructure, you can gain insight into normal and abnormal behaviors on your network, protect sensitive data, and prevent unauthorized access.
In the following blog, we’ll define UEBA, explain what threats this tool prevents, and discuss how Plixer leverages its existing full NDR security platform to provide effective behavior analytics.
What is UEBA?
UEBA is a cybersecurity technology that focuses on monitoring and analyzing behaviors from users and entities within an organization. It can collect data from various sources – log files, network traffic, applications, and endpoints – to establish a baseline of normal behavior, using ML algorithms to identify any deviations from the norm. Alerting on these anomalies aids security teams that employ UEBA in their detection of and response to potential breaches.
When anomalies are detected, UEBA systems typically assign some sort of “risk score” to the event. This score can be determined from multiple factors, like severity or context. For example, excessive authentications from admin users would likely warrant a higher risk score. High-risk anomalies that surpass a configured threshold can trigger alerts for an organization’s security team, prompting further investigation. Teams can even use rule-based automation for high severity events to mitigate risk before a security professional is available to intervene.
UEBA often combines data from other tools to enhance overall security posture. User and entity behaviors from cloud providers, IAM services, SIEM systems, and EDR vendors could be leveraged for UEBA machine learning algorithms. This integration allows for a more centralized and contextual approach.
The goal of UEBA solutions is to detect anomalous or suspicious activity from users and entities in real time. Aggregating and analyzing data from diverse sources (sometimes including visibility into third-party data) provides a comprehensive view of behaviors across an organization’s IT landscape.
The Value of UEBA
UEBA can be a powerful addition to your organization’s cybersecurity toolbelt, catching anomalies and reducing the impact of breaches that would otherwise go undetected by existing security measures. It has the potential to address several critical challenges faced by security professionals today:
- Data breaches: prevent unauthorized access to sensitive data such as PII, financial statements, user authentications, partnerships, and intellectual property by identifying abnormal access patterns and data exfiltration attempts
- Insider threats: whether intentional or due to compromised credentials, stop malicious activity in real time by noticing subtle deviations in behavior that may indicate an ongoing attack
- Advanced threats: detect sabotage or disruption attempts from bad actors, even if they employ tactics to evade traditional security controls
- Compliance: gain visibility into user data to aid in compliance with regulatory requirements or audits
- Zero trust: align with Zero Trust principles by focusing on behavior-based access controls and enabling continuous monitoring
- Hybrid environments: analyze behaviors across complex on-prem, cloud, and remote endpoint configurations that aren’t covered by traditional approaches
- Cybersecurity shortages: leverage ML and empower security teams to use their resources efficiently with automated threat detection and response processes
In summary, UEBA makes use of behavior-based analytics and machine learning to uncover suspicious user or entity behavior.
UEBA with Plixer One(TM)
User and Entity Behavior Analytics (UEBA) with Plixer One takes advantage of its existing platform to protect organizations across multiple user access points. Active Directory, Azure, and Office 365 authentications are monitored to detect suspicious activity and report any indicators of compromise. These alarms cover excessive authentications, inconsistent geographic logins, an unusual number of hosts a user authenticates from, and logins from new privileged user accounts. It also gives visibility into both interactive and non-interactive authentications.
Machine learning is key for monitoring user behaviors and detecting insider threats. Behavioral data (from the sources mentioned above) is used to create ML models, establishing a baseline for “normal” user behavior. Any deviations can be flagged as anomalies. Plixer UEBA users can get started right away with out-of-the-box analytics or opt for more fine-grain, customizable risk models – thresholds and sensitivity levels are adjustable, empowering your security team to investigate actual incidents and avoid the noise of false positives.
Combining UEBA with flow data collection gives a comprehensive view of LDAP and cloud users and entities. To detect insider threats like data accumulation and data exfiltration, the ability to associate a user or host with an IP address is paramount: mapping specific hosts and locations to users or entities allows security professionals to employ selective packet capture, using rules to capture traffic for further investigation. Capturing specific data from risky users eliminates the need to store and process the enormous amount of packet data on any given organization’s network.
Security teams can also integrate UEBA with any existing SIEM products to correlate abnormal events and provide additional context. ML algorithms and flow-based analysis uncover anomalies without the need for signature matching, employed by traditional security platforms. Plixer UEBA is proactive against threats, detecting subtle changes in behaviors instead of waiting for signatures – combining UEBA with traditional SIEM systems produces a full-coverage solution.
Finally, Plixer UEBA and Scrutinizer make a powerful team. You’ll find easy-to-navigate reports categorized by LDAP, Azure, and Office 365 logins, along with alerts integrated into the Scrutinizer dashboard. Drill into any alerts to see relevant flow data: timelines, violator IPs, usernames, successful and failed logins, locations, number of logins, and more. See user and entity data associated with specific alerts, or run a report within a desired timeframe to stay ahead of suspected threats. Scrutinizer’s unmatched network performance monitoring joined with Plixer One Security UEBA means your organization can respond to authentication-based breaches with speed and scale.
Examples
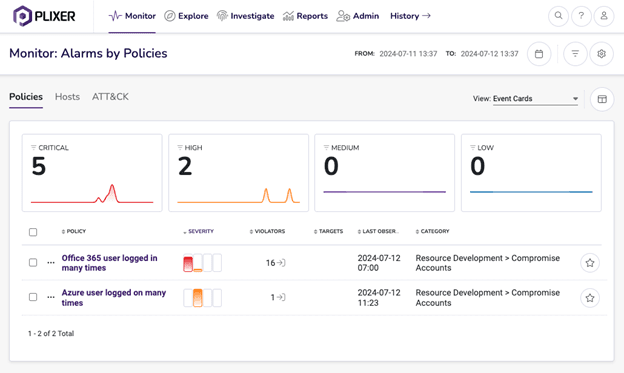
Plixer One dashboard showing alarms related to user/entity behavior
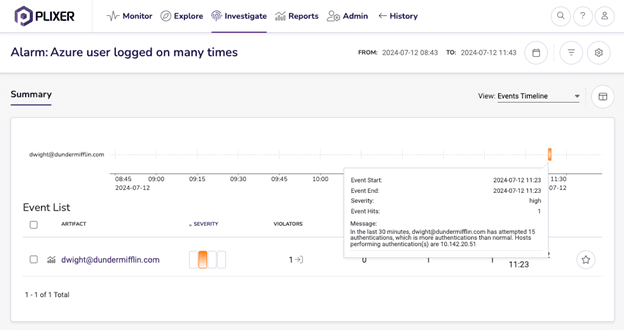
Drilling into an Azure excessive authentications alarm
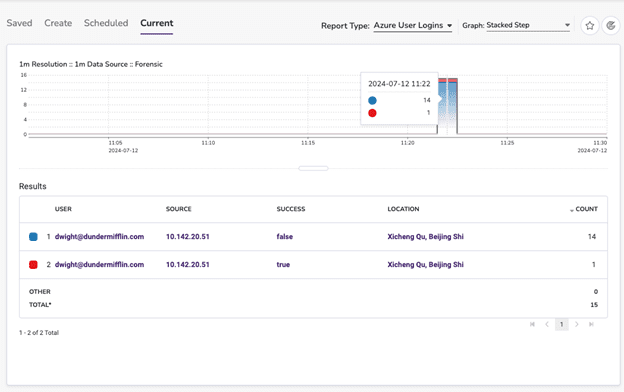
Exploring event traffic for the alarm via report
Stop Threats with Plixer One
We’ve learned that UEBA is a cybersecurity technology focused on detecting unusual user behaviors, enhancing your organization’s ability to detect authentication-based anomalies. The Plixer One platform takes advantage of machine learning algorithms to create a baseline of user behavior, then alerts on any deviations from the norm in the Scrutinizer UI. This new feature reduces risk and aids security teams in identifying and responding to suspicious user activities.
Ready to enhance your security infrastructure with UEBA? Stop threat actors in their tracks and keep your business protected – schedule a demo with Plixer today to see how you can strengthen your defenses against advanced user-based threats.