Detecting VPN traffic on the network is a use case I hear daily from school systems ranging from primary schools all the way up through large universities. One of the biggest concerns for a security or network engineer is tracking potentially unwanted traffic on the network. This could be something harmless but forbidden like video games, or a major threat like the latest APT that was just uncovered. This is why we implement strict ACLs and segregated VLANs on the network, and why we look at things like Deep Packet Inspection (DPI) as well as SSL DPI to help us gain insight into encrypted traffic. This blog aims to go over a couple technologies you probably already have at your fingertips and how you can use IPFIX/NetFlow analytics to track this nefarious behavior.
What is VPN traffic and why do I care?
Alright, in the very likely case that you know what a VPN is, you are probably asking yourself, “Why should I need to track this?” For starters, it can allow end users to bypass your firewall and do whatever they please. This often includes gaming, BitTorrent over VPN (downloading copyrighted material in most cases), and video streaming sites. So unless you have a very open policy when it comes to internet practices in the office, you might want to consider monitoring or even blocking VPN traffic altogether.
Detecting VPN traffic
You may think that blocking certain ports and protocols is a surefire way of blocking the traffic from going through your network. That works some of the time, but most of the time it won’t. This is because the utilities are essentially made to bypass some sort of firewall, whether it be geo-blocking certain countries or for encryption of your traffic so certain agencies can’t view it. Either way, they have crafty ways to disguise this traffic as “normal” network behavior.
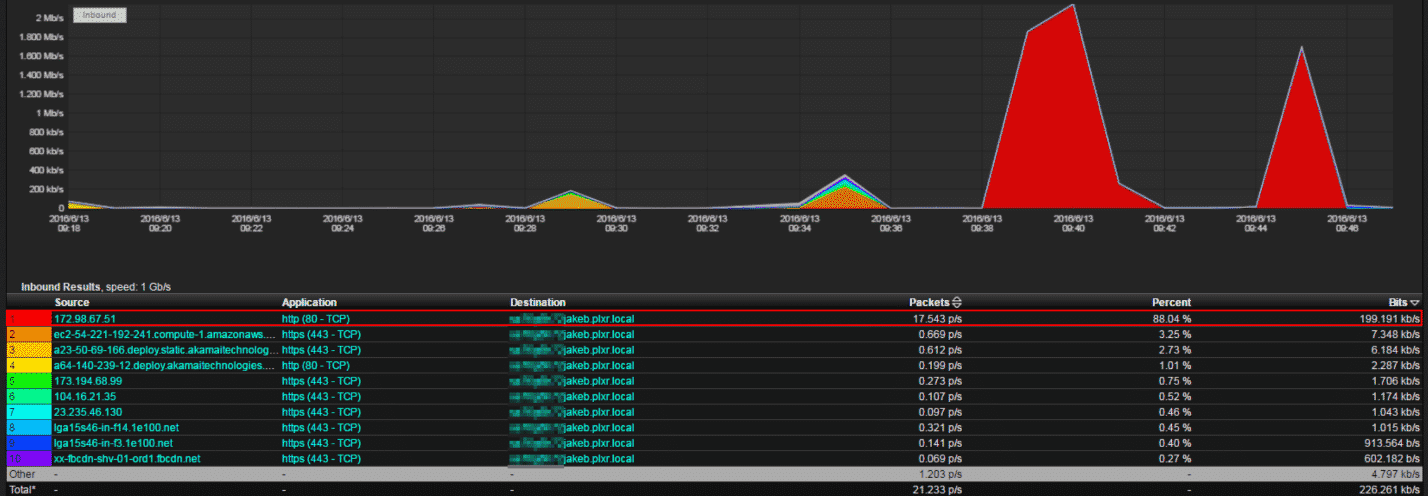
Take the above image. Most network/security engineers would look at this and say, “It looks like web traffic.” Why? Because it’s running on port 80, which IANA defines as the port that is used for HTTP traffic. Well, I hate to burst your bubble, but it’s not—it’s actually Jake streaming Netflix in the office (with proper permission). But this is using NetFlow v5 and not IPFIX, which can help give us more insight using DPI.
Now let’s look at the image below.
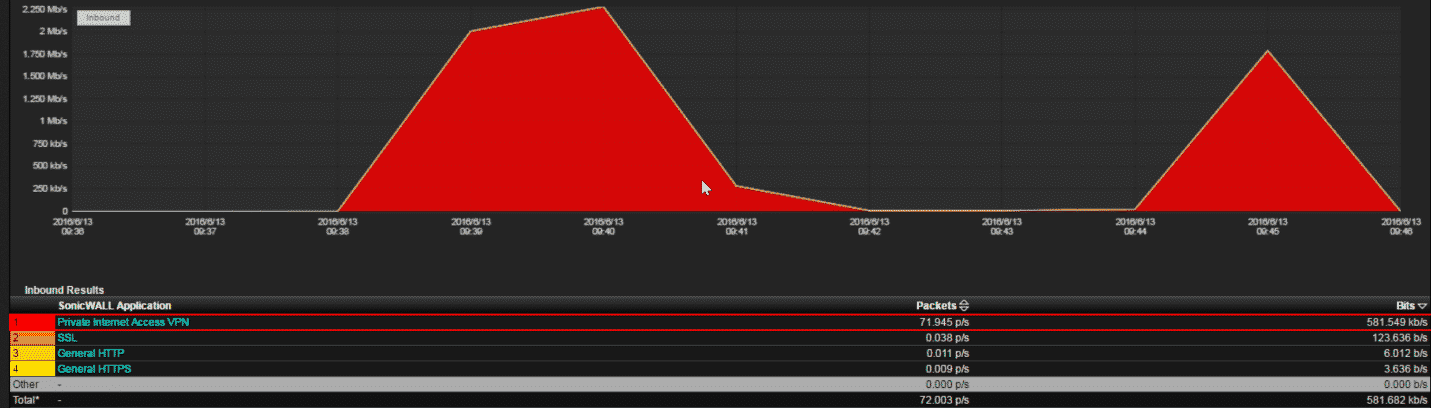
This image shows the same traffic as before. Instead of using NetFlow v5, however, I used DPI exported from our firewall, which correctly identifies the vendor of the VPN Jake is using. Since it’s still encrypted and being tunneled, I can’t easily see what services are used, but I can tell that we have a rogue VPN user on our network and block the traffic.
VPN users and you
While there are lots of legitimate uses for private VPN connections, like using it to safely browse public internet connections, we often see people abusing it. When it’s on the network that you control, this is something that shouldn’t be taken lightly. Using DPI, we can quickly and easily track this behavior right down to the user that is doing it and when they did it.
If you need any help setting up IPFIX with DPI functionality feel free to reach out to our support team!


