Detecting TOR traffic will help identify possible infections on your network. It keeps the eyes of your network team open to different types of malware that utilize Tor for disguising its intent end location. Tor not only encrypts its traffic, but also disguises its traffic as HTTPS communications thus making NetFlow/IPFIX a valuable asset in setting this traffic apart from normal HTTPS traffic that we all know is on the network.
What is Tor?
Tor, short for The Onion Router, is a collection of servers developed by the U.S Navy that allows people to browse the web with anonymity. The traffic is passed between different TOR servers where it is encrypted so the traffic can’t be traced back to where the conversation originated. Tor is a great technology for hackers that want to get into your network and exfiltrate sensitive data without leaving a trail leading right back to their location.
How Malware May Utilize Tor
Different types of malware will use Tor nodes for their communications’ command and control server on the anonymous network. The Onion malware, for example, is a type of ransomware that is the successor to the well-known CryptoLocker. The Onion malware will encrypt the user’s data, and demand payment be made within a strict time-frame for the data to be decrypted.
“Now it seems that Tor has become a proven means of communication and is being utilized by other types of malware. The Onion malware features technical improvements on previously seen cases where Tor functions were used in malicious campaigns.” said Fedor Sinitsyn, Senior Malware Analyst at Kaspersky Lab.
Detecting TOR Traffic on your Network
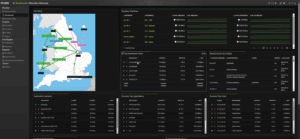
With the use of NetFlow/IPFIX, we can identify the Tor traffic that is on your network, and send alerts regarding who is trying to be anonymous. With a list of Tor exit nodes, we can tell our NetFlow/IPFIX collector to set up a policy that will trigger if any of these IPs are identified as a source or destination of any traffic on our network. Our incident response system includes such a list, and also the policy that will search for this traffic. If you to wish to get a similar list of known Tor exit nodes, you can get one from https://www.dan.me.uk/tornodes.
The image below is of our policy that was set up to display both the end user, which is in communication with a known Tor server, and the server itself. With this policy we can now set up an email alert to notify the network administrators to further investigate the possible infection.
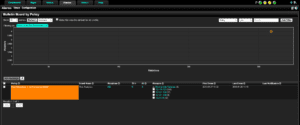
When it comes to network security, detecting Tor traffic will help network administrators investigate suspicious traffic and determine if the traffic is unwanted or not.