A rogue DHCP server on a network is one that is not under the administrative control of the network staff. It can be a network device such as a modem or a router connected to the network by a user who may be either unaware of the consequences of their actions, or may be knowingly using it for attacks on the network.
As clients connect to the network, both the rogue and legal DHCP server will offer them IP addresses as well as the addresses of the default gateway and DNS servers. If the information provided by the rogue DHCP differs from the real one, clients accepting IP addresses from it may experience network access problems, including speed
issues as well as inability to reach other hosts because of an incorrect IP network or gateway. In addition, if a rogue DHCP is set to provide as default gateway an IP address of a machine controlled by a misbehaving user, he can sniff all the traffic sent by the clients to other networks, violating network security policies as well as user privacy.
A common rule of thumb for any network using DHCP is to only use one DHCP server, and if you must use more than one to make sure the IP ranges being handed out do not overlap. However, just because you only have one legitimate DHCP server on the network doesn’t mean that another one doesn’t exist.
There are a couple of telltale signs you can look for when you suspect another DHCP server exists on your network.
- Several of the computers on the network begin losing their IP addresses or picking up addresses that are not standard on your network.
- Due to overlapping address ranges being handed out, several machines on your network report IP address conflicts.
- You see an abnormally large amount of DHCP traffic (UDP ports 67 and 68) flowing through the network.
- Since the chances are that the rogue DHCP server is there for malicious intent, the amount of virus traffic being caught by your network’s virus monitoring system could potentially increase dramatically. Along these same lines, you could also see an increase in bandwidth utilization.
Anytime you see any of these things happen you should always consider the fact that there may be a DHCP server that exists in your network without your knowledge.
Network traffic monitoring using flow technologies to monitor communication behaviors, maintaining baselines, and detecting advanced persistent threats is becoming more relevant.
Collecting and analyzing NetFlow provides an easy monitor and alarm solution to combat a rogue DHCP server issue.
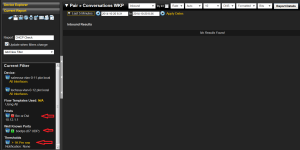
By creating a report that filters on UDP port 67, and excluding (by either IP address or MAC address) the address of the legitimate DHCP servers, you get a quick picture of any conversations on your network that may involve rogue DHCP servers.
Notice in the report below that we have no results when the network traffic is filtered on UDP port 67, and the DHCP server IP address is excluded.
And you can also set an alarm that will alert you if any DHCP (bootps – UDP port 67) traffic is occurring.
Network forensics and incident response using NetFlow gives administrators access to all of the conversations traversing the network. When security professionals need to go back in time and view a communication pattern, they can find the flows that contain the conversations that they want to investigate.
Flow data is incredibly efficient to transmit and store. Network flows can be enabled anywhere you have a router, switch, or firewall, and the best part is that you don’t need to deploy hardware via a SPAN or tap. NetFlow and IPFIX are built in. It’s already there just waiting for you to turn it on.
Are you ready to add this type of network visibility and alarming to your monitoring solution? Give us a call and we’ll help you get NetFlow configured on your network.

