According to a recent article on BleepingComputer, a backdoor Python library can steal SSH credentials. This can lead to ssh credential misuse if undetected by IT professionals. “The module’s name is SSH Decorator (ssh-decorate), developed by Israeli developer Uri Goren, a library for handling SSH connections from Python code. On Monday, another developer noticed that multiple recent versions of the SSH Decorate module contained code that collected users’ SSH credentials and sent the data to a remote server located at: http://ssh-decorate.cf/index.php.” In this article, I’ll show you how to detect SSH credential misuse with network traffic analytics and your existing network infrastructure.
What is credential misuse?
To get things started, though, let’s first define what we mean when we say “credential misuse.” Credential misuse is the unauthorized or unlawful use of another person’s or entity’s credentials. The credentials can be obtained in any number of ways—even legally—but are used in a manner other than intended or authorized.
How to detect SSH credential misuse
Let’s take a look at how you can detect SSH credential misuse on your network. By doing so, I also hope to help you detect malicious actors and software (including the compromised version of SSH Decorator) on your network.
By using network traffic analytics, IT and security professionals can tap into the existing network infrastructure to baseline normal SSH behavior from every user on the network. For example, I connect to two or three different servers via SSH on our network each day. As such, our network traffic analytics platform, Scrutinizer, has baselined my normal traffic as connecting to these servers on a regular basis.
But if I connect (or simply try to connect) to any other server, Scrutinizer will alert our security team to an indicator of compromise. Let me show you what this would look like.
Let’s take a look at my normal SSH traffic first.
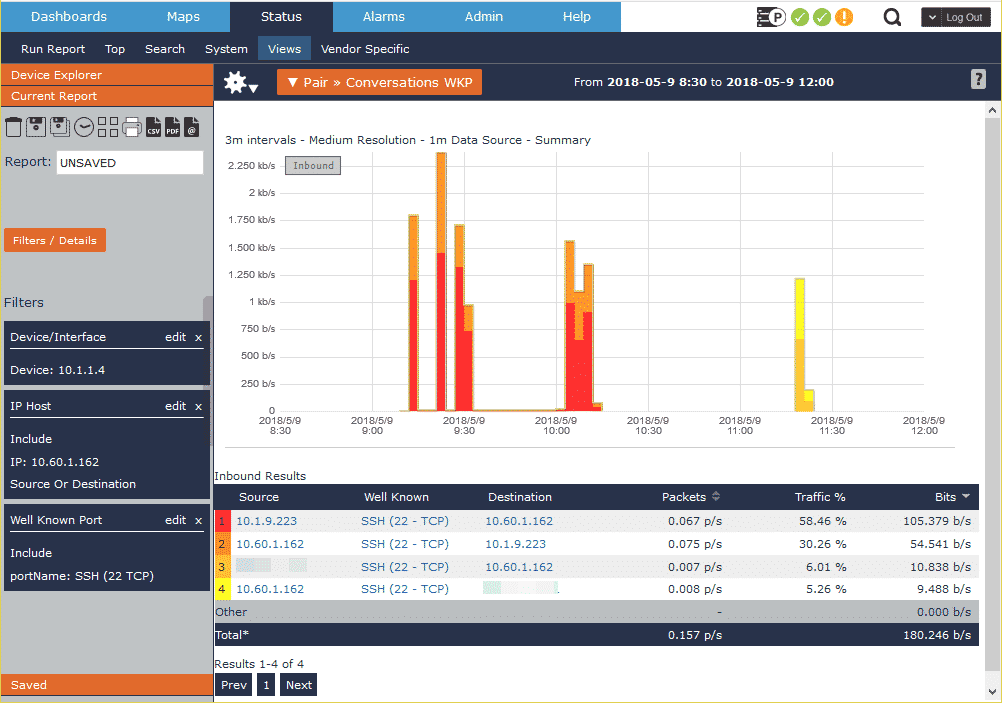
I normally connect to a public internet-facing server (obfuscated for security) and an internal development box. Because this is my normal SSH connectivity, our security and network teams know that this type of traffic is normal. If, however, I start connecting to unusual servers, the system will alert both teams to the potentially malicious activity and confirm if it’s wanted traffic.
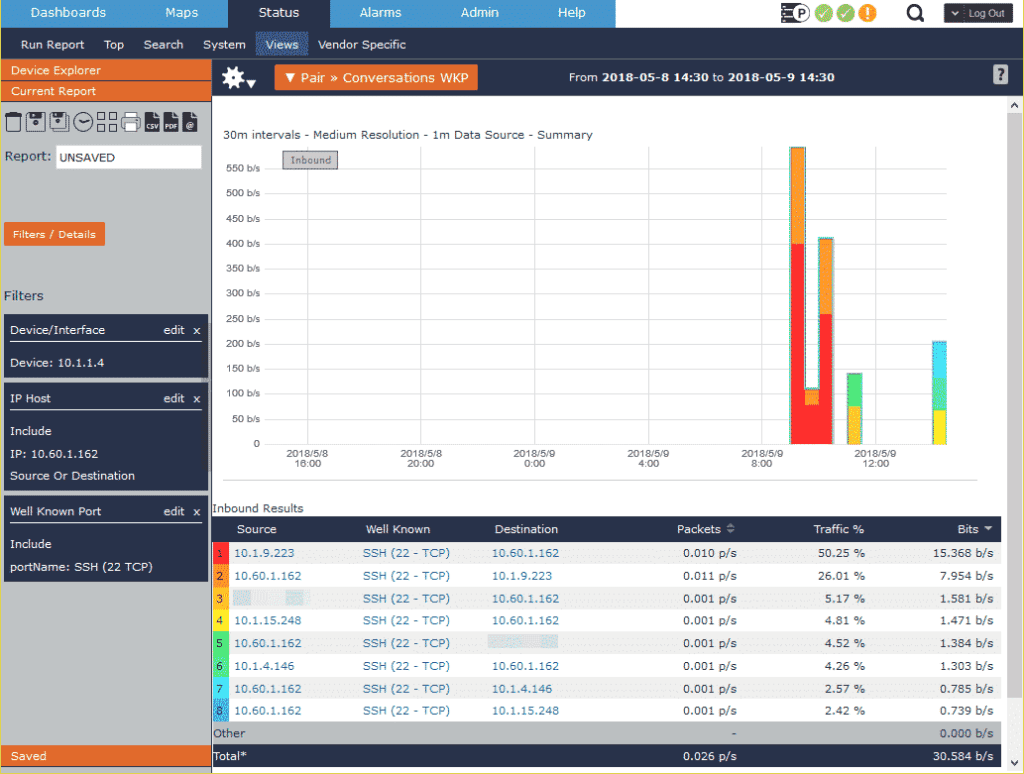
As shown in the picture above, there are now additional SSH connections that are outside of the normal traffic pattern. These connections should be investigated to determine if they were wanted. In this case, though, I was connecting to a fellow colleague’s test boxes to get some information. If this wasn’t a legitimate connection, though, it would be likely that credentials were stolen for these servers, and the passwords or keys should be changed immediately to prevent further access.
Using network traffic analytics has many benefits, including SSH credential misuse detection. If you aren’t taking advantage of network traffic analytics on your existing network infrastructure, you should be. Download a 14-day trial of Scrutinizer to get started.




