Plixer FlowPro 20.1 Release
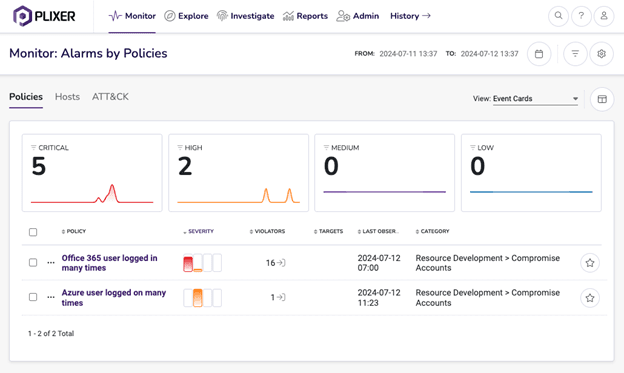
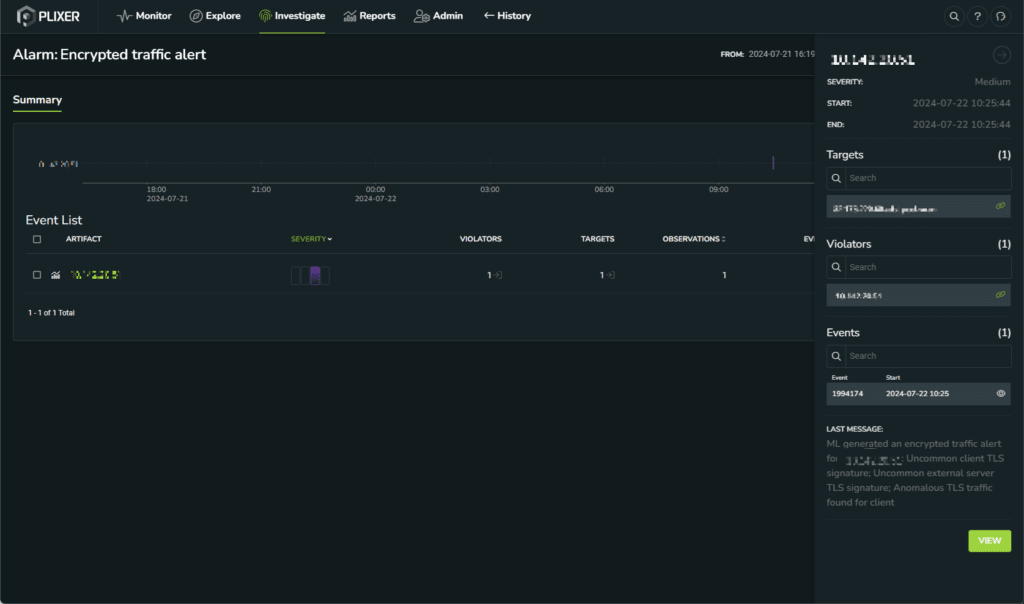
Today, we are thrilled to announce that Plixer FlowPro 20.1 is generally available! With version 20.1 FlowPro consolidates the rich capabilities of FlowPro APM and FlowPro Defender into a single hardware or virtual appliance. This combination will reduce hardware ...
Continue Reading