We recently upgraded a few of our Cisco IOS routers to version 15.4(2)T and enabled zone-based firewall logging, which allowed us to export firewall logs in NetFlow! Check out the rest of the blog on what event types Cisco supports and an example configuration!
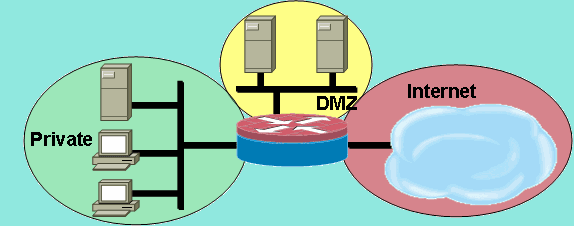
A Zone-Based Policy Firewall, also known as Zone-Policy Firewall or ZFW, changes the firewall configuration from the interface-based model to a zone-based model. Interfaces are assigned to zones, and inspection policy is applied to traffic moving between the zones. Figure 1 shows an example of these zones, here we have 3 – the DMZ, Private (LAN), and Internet (WAN) zones.
Figure 1: Basic Security Zone Topology [Source: Cisco]
Whether you already have the zones setup or are just starting out, the firewall event logs being exported in Cisco NetFlow is new for everyone (at the time of this blog)! From the Cisco documentation on Zone-Based Firewall NetFlow Support, the router can now export the following event types:
- Audit Events
- Start Audit Record and Stop Audit Record.
- Logs messages when sessions are created and deleted.
- Drop Events
- Packet Drop notifications.
- Logs messages when the following events are dropped—unknown protocols, unseen flows, Out-of-Order (OoO) packets, etc.
- Alert Events
- TCP Half Open Alert
- Half Open Session Alert
- Maximum-Open sessions
- Logs TCP half-open alert messages when the TCP half-open alert threshold values exceed the configured limit.
Now that we know the events we can collect, we need to setup the configuration on the router. The process for this as follows:
- Define a flow exporter and option templates.
- Attach the flow exporter to a global parameter map.
Zone-Based Firewall NetFlow Configuration Example
flow exporter export-to-scrutinizer description flexible NF v9 destination 10.xx.xx.xx source Loopback0 output-features transport udp 2055 template data timeout 60 option interface-table option exporter-stats option application-table option inspect-class-table option inspect-protocol-table option inspect-ext-event-table option inspect-zonepair-table
parameter-map type inspect global
alert on
log dropped-packets enable
max-incomplete low 18000
max-incomplete high 20000
exporter export-to-scrutinizer
Cisco NetFlow Firewall Logging Support
By looking at the NetFlow data, you are be able to see these Firewall events (see Figure 2). We have a pair host-to-host report showing both the firewall event and the summation of that event in the given time frame.
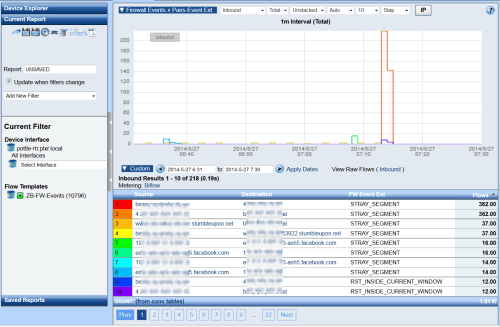
Figure 2: Cisco Zone-Based Firewall Log Export Support
We need to keep in mind some differences with this NetFlow Export. This export is a NetFlow version 9 biflow (exports both bytes and reverse bytes) and if a flow is denied it will show the conversation having 0 bytes (from reverse bytes). Also, no interfaces or no packet counters are exported. Even with these caveats, the data we can gain insight into is useful from a correlation and a security forensic investigation standpoint. Having this event data in NetFlow allows us to quickly go from firewall log events to “typical” NetFlow tuple data.
More on Firewall Logging Support
If you have any questions on setting up your Cisco NetFlow exports, feel free to reach out to the Plixer Support Team at 207-324-8805.