Are you looking for Cisco ISE NetFlow integration? We have this working with both Cisco ISE v1.2 and v1.3. In the past, we have integrated with other network authentication systems such as ForeScout’s CounterACT and Extreme’s Mobile IAM. However, by far the most popular appears to be Microsoft Active Directory.
- Q: Why are companies looking for Cisco ISE NetFlow integration?
- A: Contextual Details
Traditionally in networking, we track down end systems by searching on IP addresses. Although this sounds like a great way to narrow in on an end system, we still need to associate the host to an actual username. After all, we really want to know “who done it” and that would be the person who authenticated the device onto the network.

Until the integration with Cisco ISE and similar solutions, making the connection between the two has proven to be a bit cumbersome. However, once developers discovered a way to make the connection between IP address and username, they found a treasure chest of additional contextual details. Lets take for example some of the details we were able to extract from Cisco ISE:
$VAR1 = {
'0A01024C00000061465668D8' => {
'accessTime' => '2014-11-17T13:02:37.616Z',
'authTime' => '2014-11-17T13:02:37.341Z',
'idIPAddr' => '10.1.14.255',
'idIdGroup' => 'Unknown',
'idIdStore' => 'AD1',
'idMacAddr' => 'EC:F4:BB:47:CF:A9',
'idUser' => 'PLXR\\mikek',
'ip' => '10.1.14.255',
'location' => 'GOLD-Lab',
'mac' => 'EC:F4:BB:47:CF:A9',
'nasDevName' => '3560-cx',
'nasIpAddr' => '10.1.2.76',
'nasPortId' => 'GigabitEthernet0/5',
'user' => 'PLXR\\mikek'
Above, we can see that the IP address ‘idIPAddr’ is 10.1.14.255 and the associated username ‘idUser’ is mikek. When searching for an end system, the ability to associate the IP address with the username that authenticated it onto the network is a real time saver however, as you can see above, we don’t have to stop here. Why not search on username instead of the IP address. We are also providing details on:
- When the user authenticated onto the network ’authTime’
- Where they authenticated from ‘location’, switch ‘nasDevName’, interface ‘nasPortId’ and details such as ‘mac’ address.
- Some authentication systems even report back the type of device (e.g. iPhone, Android, Cisco Phone, etc.)
Loaded with the above, we can start to marry the details provided by Cisco ISE with the NetFlow, IPFIX and even sFlow data that is exported by the hardware that is supporting the traffic from the devices authenticating onto the network.
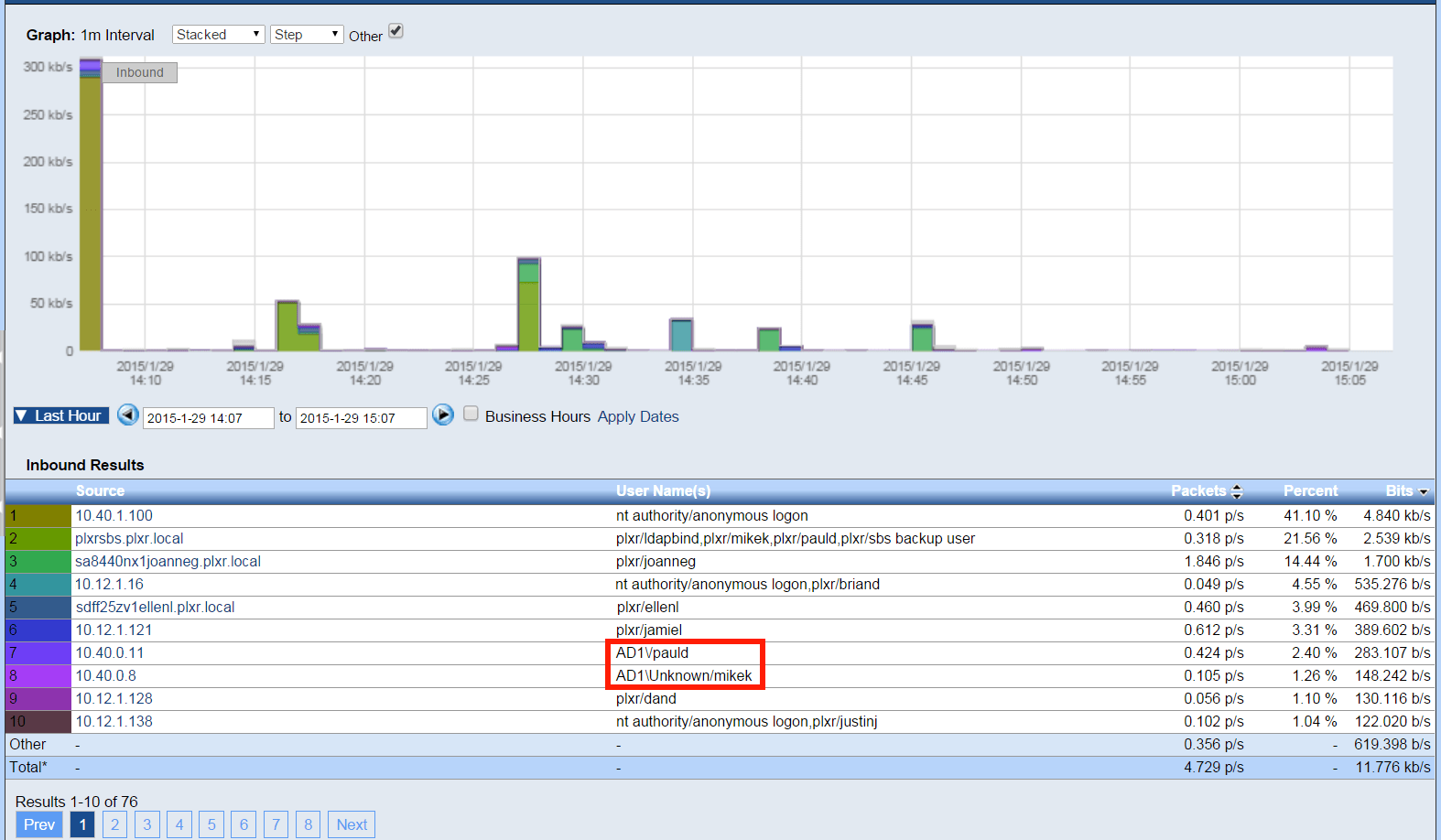
Above you can see the entries boxed in red start with AD1\ which tells us that the host authenticated onto the network via Cisco ISE. The other end system usernames were collected using Microsoft Active Directory. We can support multiple authentication systems simultaneously. Below is another report we are working on.
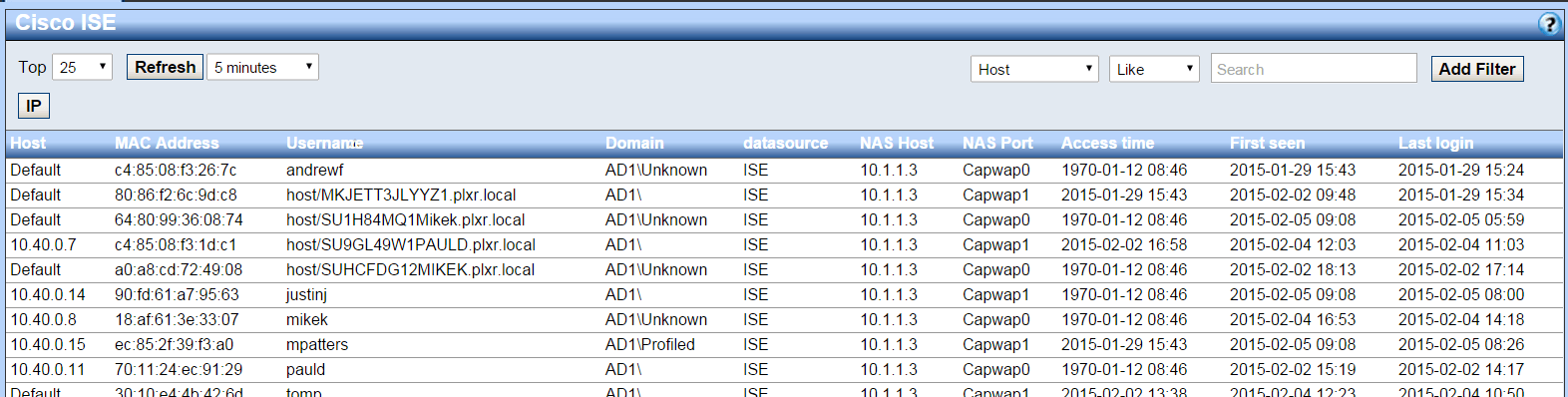
With all of the above details, the administrator can quickly apply policy to determine next steps (e.g. remove the users access to the network) this of course is dependent on the reported behavior that led to the investigation. Monitoring for abnormal communication behaviors is one of the responsibilities of our malware incident response system.
During the integration process we learned that in Cisco ISE 1.3 there is no REST API documentation which means that we have to work with pxGrid. The upside is that we gained access event logs which we are looking to do more with.
At this point, we are exploring Scrutinizer functionality which would allow the administrator to remove users from the Cisco ISE system. For example, if an alarm occurs, we could provide the ability to automate the disconnection from the network. Give us a call if you would like to set this up or if you have suggestions on how to improve the integration.

