Recently, we tested Cisco ISE vs Forescout CounterACT. We have implemented and integrated our Incident Response System with three different authentication systems like this and this post highlights some of the features and facts that we really liked about CounterACT v7.0.0.
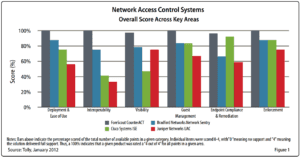
We have worked and integrated with Cisco ISE v1.2 as well as Extreme’s Mobile IAM solution. We contacted Cisco several times about their v1.3 release, but they did not get back to us. Similar to what the Tolly Group published about ForeScout CounterACT Vs. Cisco ISE back in March of 2012, we really like the CounterACT solution for several reasons.
- no dependency on 802.1x
- very easy to configure < less than 8 hours
- little operational impact once it is deployed
- provides many built in classifications and remediation options
- worked with switches from all of our different vendors. We like our Cisco hardware, but we are not all Cisco.
- easily enhanced the protection of our mobile environment
- no infrastructure upgrades
- no agent to install on systems wanting to access the network
- ability to correctly identify devices (e.g. smart phones) via hijacking or other non agent method
- in-line deployment is optional
- ease of compatibility with devices like printers and desk phones without blocking them by default
- ease of classifying devices into types of devices or departments
The Tolly engineers evaluated 34 criteria across 6 categories and ForeScout CounterACT scored the highest.
Many of our customers have purchased some type of NAC authentication system. When we ask them if they want to integrate the contextual details they collect with our system ‘Scrutinizer’ they almost always reply with the same answer “we don’t have NAC solution setup yet because we ran into some problems”. My fear is that the expensive system they purchased will eventually become shelf ware. CounterACT customers do not appear to be experiencing this nearly as much as other vendors. This was an important point because we wanted to integrate with something that people were actually using and appreciating the value of after deploying.
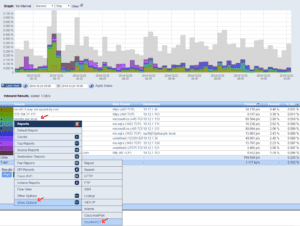
The CounterACT API was straight forward to integrate with. In fact, what we wanted to do was simply URL driven and we had the basic integration shown below set up in a day. Notice below, you can click on a host, and follow the menu options to ‘CounterACT’.
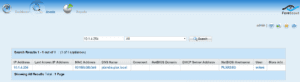
Once you select the above CounterACT menu option, the ForeScout interface appears. Notice below that we pass the IP address to CounterACT which it uses to look up contextual details about the host viewed in our NetFlow collection system ‘Scrutinizer’.
Although the integration at this level is fairly simple, this simple passing of variables to another application makes life easier for many engineers that use both of our products. If you have questions about this integration or if you would like to try it, please reach out to our team.