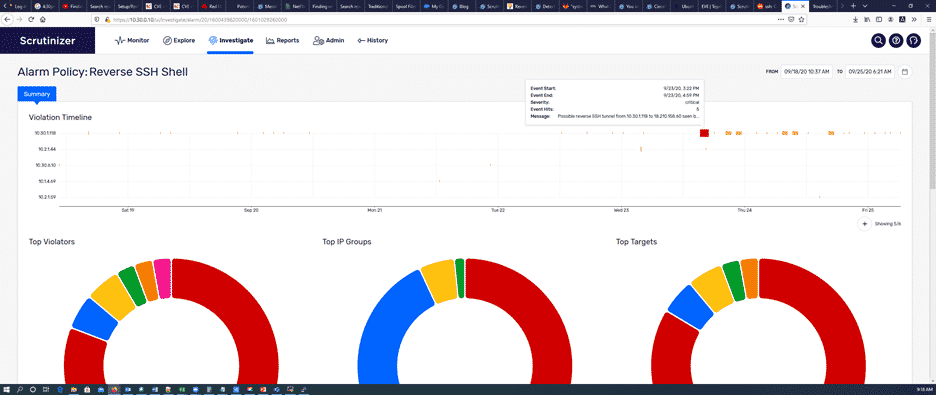
How to detect a reverse SSH tunnel
Today we are going to talk about Plixer’s new Flow Analytics algorithm, Reverse SSH Shell, which has been included in the latest Plixer Scrutinizer...

Today we are going to talk about Plixer’s new Flow Analytics algorithm, Reverse SSH Shell, which has been included in the latest Plixer Scrutinizer...

What is STIX/TAXII? STIX stands for Structured Threat Information Expression, which is an open-source language and serialization format used in sharing threat intelligence. Think...
I can’t tell you how many calls I’ve been on where the NetOps and SecOps teams really don’t know what the other is doing....

Many ISPs filter bogon connections because bogon IP addresses have no legitimate use. If you find a bogon or bogus IP address in your...

A common tactic for bad actors to get a foothold into the network is to leverage IP spoofing to either: Regardless of the intention,...

How safe is your personal information? Well, several celebrity clients of a New York law firm have discovered that it’s only as safe as...
How do you know who’s accessing your data? Do you know if your data has been copied to other locations? Have you put enough...

In our first roundup post of the decade, I’ve included interesting articles whose topics include hacking satellites, the difference in mindset between technologists and...

We’ve all had days when we think to ourselves, “Man, I wish I could just work from home in my PJs.” Recently, as companies...
Almost every organization is equipped with VPNs to support a remote workforce these days. Often, secure VPNs use a no-split secure tunnel, tunneling all...