
Understanding Lateral Movement: How Attackers Navigate Your Infrastructure
Lateral movement refers to the techniques attackers use to move through a network after gaining initial access. Instead of attacking a single machine, they...

Lateral movement refers to the techniques attackers use to move through a network after gaining initial access. Instead of attacking a single machine, they...
As we navigate through 2024, the cybersecurity landscape is increasingly dominated by stealth and sophistication. The recent CrowdStrike Global Threat Report highlights a dramatic...
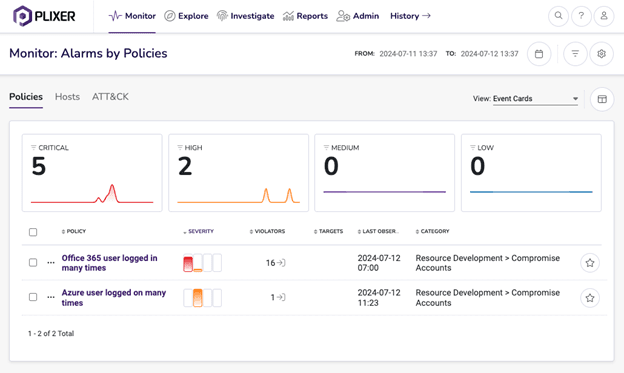
User and Entity Behavior Analytics (UEBA) provides the critical insights needed to identify these hidden dangers by monitoring behavioral patterns across users and entities,...

Author: Ryan Mellmer, Plixer Software Engineer The world is currently in an AI (Artificial Intelligence) revolution. AI is everywhere today; in the news, in...

Author: Stephanie Kille, Customer Success Manager, Plixer Recent years have seen a disturbing trend of healthcare data breaches, with cybercriminals targeting organizations across the...

The digital landscape can sometimes seem a bit like a dense forest after dark, with new and unseen threats potentially lurking everywhere. That’s why...

Any security analyst will tell you that the most challenging part of the job is knowing what to respond to. There is no shortage...

Data security is a critical aspect of any organization’s IT infrastructure. With the explosion of cyber threats, it has become ever-important to ensure that...

How prepared for an attack are you? The most recent Microsoft Defence Report found volume of password attacks has risen to an estimated 921...

XDR stands for eXtended Detection and Response. What it is depends on who is explaining it. XDR evolved very quickly from Network Detection and...