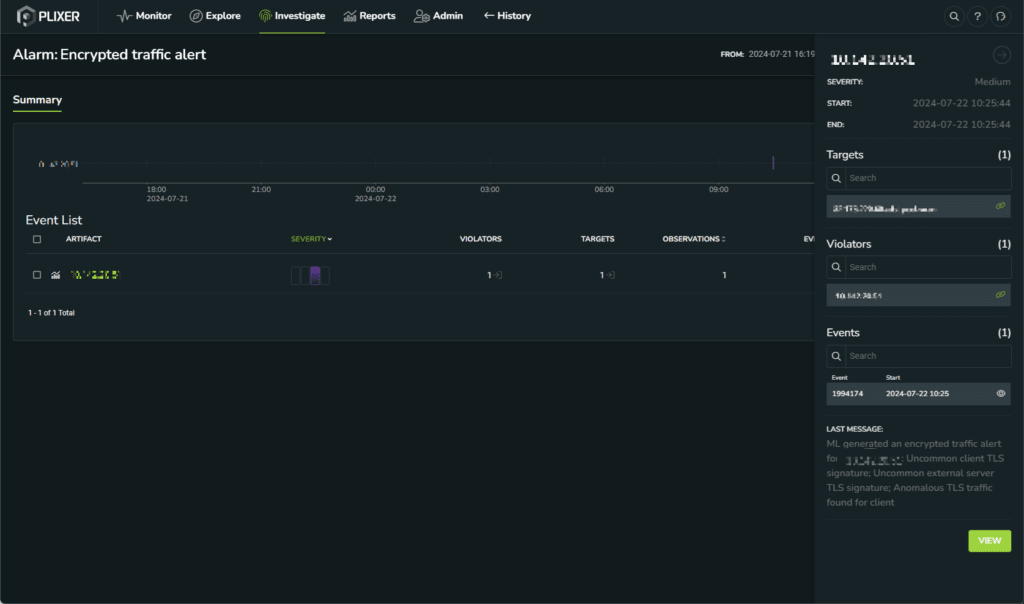
How Enterprises Elevate Networks Cost-Effectively and with Ease
In today’s rapidly evolving business landscape, enterprise networks are the lifelines of organizational operations. From enabling seamless communication among distributed teams to supporting critical...